Another neat addition to end-to-end encrypted email client ProtonMail: It’s added a zero-access encrypted contacts manager that also digitally signs the contact info you store in it. The new features have been added to v3.12 of ProtonMail’s web client, with the Swiss-based startup saying it’s working on also bringing the […]
Cybersecurity
Intel Q3’17 ME 11.x, SPS 4.0, and TXE 3.0 Security Review Cumulative Update
Intel Q3’17 ME 11.x, SPS 4.0, and TXE 3.0 Security Review Cumulative Update Intel ID: INTEL-SA-00086 Product family: Various Impact of vulnerability: Elevation of Privilege Severity rating: Important Original release: Nov 20, 2017 Last revised: Nov 22, 2017 Summary: In response to issues identified by external researchers, Intel has […]
Biggest Cybersecurity Threats for 2018
IBM recently announced the shocking average cost of data breach. While down around 10 percent, the global average for a data breach is $3.62 million. For many companies, the cost of suffering a cyberattack is enough to take the business down entirely, so it has never been more vital for […]
PHISHING BIGGEST THREAT TO GOOGLE ACCOUNT SECURITY
Last year may have been mostly about ransomware, but it’s difficult to forget the billion or so passwords that were spilled in high-profile breaches and credential leaks. Google and researchers from the University of California Berkeley attempted to ease some of that pain, and teamed up to analyze how cybercriminals […]
Android security: Google cracks down on apps that want to use accessibility services
Android security: Google cracks down on apps that want to use accessibility services Google has told Android developers that they won’t be able to publish their applications on the Google Play store if the app uses accessibility services for anything other than its intended purpose. Officially, accessibility services is an […]
Google launched Google Play Security Reward bug bounty program to protect apps in Play Store
Google has launched Google Play Security Reward, the bug bounty program that will pay $1,000 rewards for flaws in popular apps. Google has officially launched a bug bounty program for Android apps on Google Play Store, a measure that aims to improve the security of Android apps. The initiative, called Google Play […]
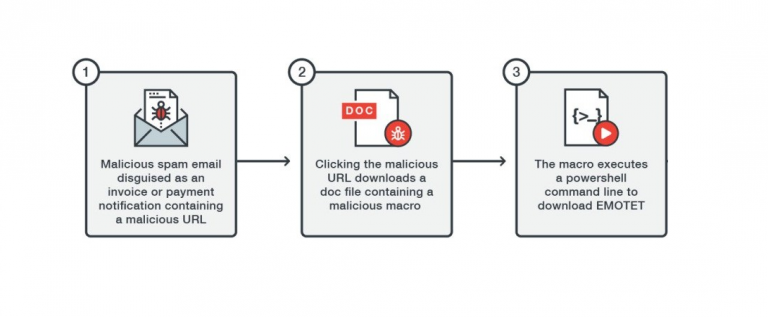
URSNIF spam campaign expose new macro evasion tactics
Trend Micro recently observed a new campaign leveraging the Ursnif banking Trojan using new malicious macro tactics payload delivery and evade detection. Researchers at Trend Micro have recently spotted a new campaign leveraging the Ursnif banking Trojan featuring new malicious macro tactics for payload delivery. Malicious macros are widely adopted by crooks […]
Microsoft Kept Secret That Its Bug-Tracking Database Was Hacked In 2013
It was not just Yahoo among « Fortune 500 » companies who tried to keep a major data breach incident secret. Reportedly, Microsoft had also suffered a data breach four and a half years ago (in 2013), when a « highly sophisticated hacking group » breached its bug-reporting and patch-tracking database, but the hack was never […]
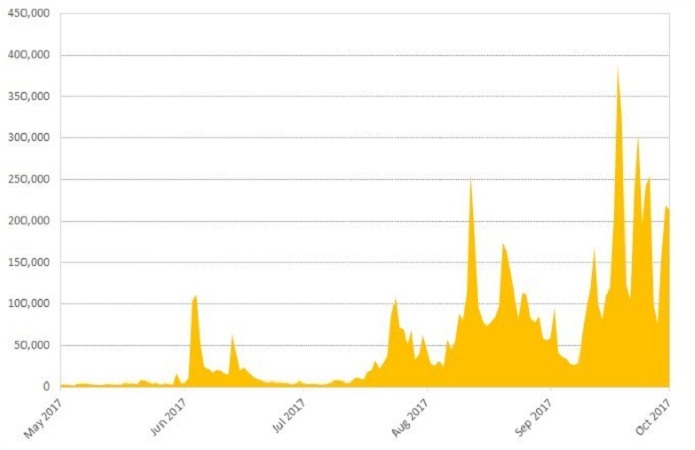
The Necurs botnet is back spreading a downloader with new interesting features
The Necurs botnet is spreading a new downloader that takes screenshots of the victims’ desktops and Runtime Errors back to the operators. The Necurs botnet is back once again, the dreaded botnet was spreading a downloader that takes screenshots of the victims’ desktops and Runtime Errors back to the attackers. “Recently we have seen […]
Plusieurs cas de cyberfraudes financières signalés au Maroc
Des cybercriminels ont récemment usurpé la qualité de présidents d’entreprises marocaines pour ordonner des virements encaissés à l’étranger. Une victime, un consultant en cybercriminalité et un banquier se sont confiés à Médias 24, pour nous éclairer sur cette arnaque des temps modernes Depuis le mercredi 17 février, plusieurs entrepreneurs marocains […]