Security experts at Flashpoint confirmed the availability online for the source code of the TreasureHunter PoS malware since March. The researchers found evidence that the threat has been around since at least late 2014. TreasureHunt was first discovered by researchers at the SANS Institute who noticed the malware generating mutex names to evade detection. TreasureHunt enumerates the […]
Haythem Elmir
NEW FACEBOOK-SPREAD MALWARE TRIGGERS CREDENTIAL THEFT, CRYPTOMINING
A new malware campaign rapidly spreading via Facebook is infecting victims’ systems to steal their social media credentials and download cryptomining code. The malware, dubbed Nigelthorn by the Radware researchers who first discovered it, is being propagated via socially engineered links on Facebook. It has been active since at least […]
5,000 Routers With No Telnet Password. Nothing to See Here! Move Along!
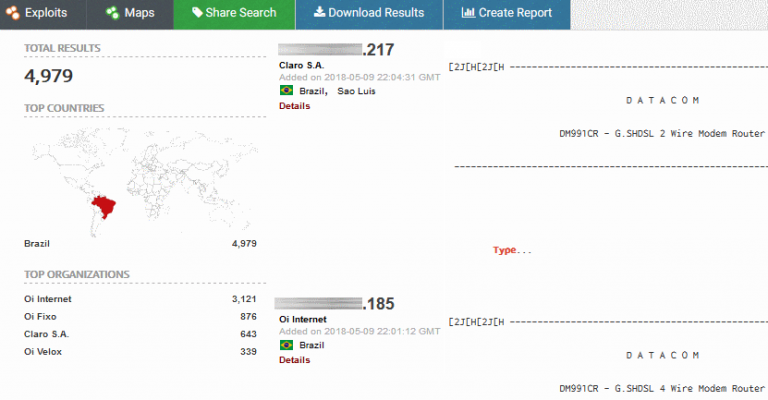
A Brazilian ISP appears to have deployed routers without a Telnet password for nearly 5,000 customers, leaving the devices wide open to abuse. The devices have been discovered this week by Ankit Anubhav, Principal Researcher at NewSky Security, a cyber-security company specialized in IoT security. All exposed devices are Datacom routers the […]
IBM Bans the Use of Removable Drives to Transfer Data
IBM has allegedly issued a worldwide ban against the the use of removable drives, including Flash, USB, and SD cards, to transfer data. This new policy is being instituted to prevent confidential and sensitive information from being leaked due to misplaced or unsecured storage devices. According to a report by TheRegister, […]
5 Powerful Botnets Found Exploiting Unpatched GPON Router Flaws
Well, that did not take long. Within just 10 days of the disclosure of two critical vulnerabilities in GPON router at least 5 botnet families have been found exploiting the flaws to build an army of million devices. Security researchers from Chinese-based cybersecurity firm Qihoo 360 Netlab have spotted 5 botnet families, […]
Bitcoin Wallet App Caught Stealing Seed Keys
The team behind Electrum, a Bitcoin wallet app, has exposed a copycat product named Electrum Pro as a malicious app that steals users’ seed keys. Electrum developers made their accusations in a document published on GitHub yesterday. The document contains a step-by-step guide to decompiling a rival product named Electrum Pro that popped up online […]
Oh, Joy! Source Code of TreasureHunter PoS Malware Leaks Online
On the malware scene, there is no clearer sign of trends to come than the leaking of a malware family’s source code. Based on this assumption, we can now expect an influx of Point-of-Sale malware in the coming months after the release of the source code of the TreasureHunter PoS […]
Faster Payments: Effective Fraud Mitigation Strategies
The Faster Payments Task Force is working toward launching a real-time payments network in the U.S. by 2020. But faster payments could open the door to more fraud, as has been experienced in other countries, such as the U.K. and Mexico. Meanwhile, the U.S. has already experienced fraud exploits on a […]
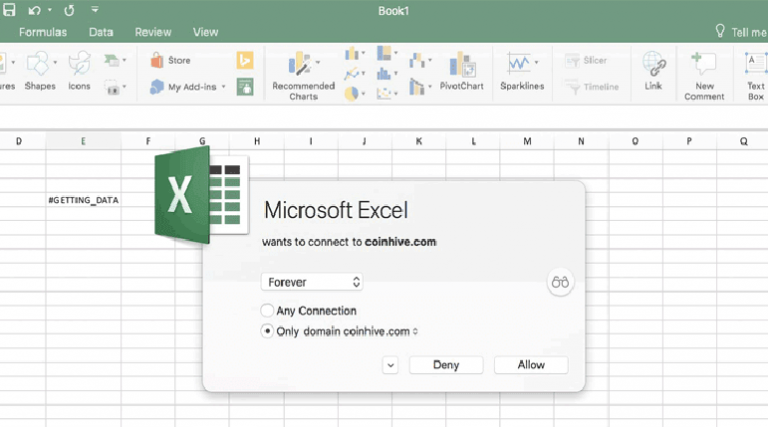
Microsoft Adds Support for JavaScript in Excel—What Could Possibly Go Wrong?
hortly after Microsoft announced support for custom JavaScript functions in Excel, someone demonstrated what could possibly go wrong if this feature is abused for malicious purposes. As promised last year at Microsoft’s Ignite 2017 conference, the company has now brought custom JavaScript functions to Excel to extend its capabilities for better work […]
Are you using Python module ‘SSH Decorator’? Newer versions include a backdoor
A backdoor was discovered in the Python module named SSH Decorator (ssh-decorate), that was developed by Israeli developer Uri Goren. Are you using the Python module ‘SSH Decorator’? You need to check the version number, because newer versions include a backdoor. The library was developed to handle SSH connections from Python code. […]