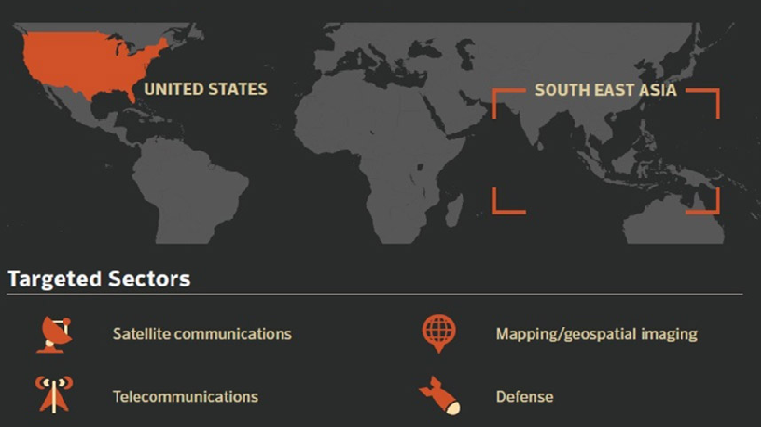
Symantec’s artificial intelligence-based Targeted Attack Analytics uncovers new wide-ranging espionage operation. One of the most significant developments in cyber espionage in recent years has been the number of groups adopting “living off the land” tactics. That’s our shorthand for the use of operating system features or legitimate network administration tools […]
Haythem Elmir
ZeroFont phishing attack can bypass Office 365 protections
ZeroFont phishing attack – Crooks are using a new technique that involves manipulating font sizes to bypass Office 365 protections. According to cloud security firm Avanan, one of the detection mechanisms in Office 365 involves natural language processing to identify the content of the messages typically used in malicious emails. […]
Olympic Destroyer was involved in a new wave of cyber attacks
Olympic Destroyer, the malicious code that was used in attacks against Winter Games in Pyeongchang, was involved in a new wave of cyber attacks. The same malware used in recent Olympic Winter Games in Pyeongchang, tracked as Olympic Destroyer, has been used in a new wave of attacks against organizations in Germany, […]
Hackers Steal $31 Million from South Korean cryptocurrency exchange Bithumb
Just weeks after Korean exchange Coinrail was hacked, the Bithumb crypto exchange was hacked, crooks stole over $30 million in cryptocurrency. It has happened again, for the second time in a year, the cryptocurrency exchange Bithumb has been hacked. The South Korean cryptocurrency exchange confirmed that hackers stole 35 billion won […]
New Telegram-abusing Android RAT discovered in the wild
ESET researchers have discovered a new family of Android RATs (Remote Administration Tools), that has been abusing the Telegram protocol for command and control, and data exfiltration. Investigating what at first seemed like increased activity on the part of the previously reported IRRAT and TeleRAT, we identified an entirely new malware family that […]
TRON Cryptocurrency Founder Buys BitTorrent, µTorrent for $140 Million
BitTorrent, the company which owns the popular file-sharing client uTorrent, has quietly been sold for $140 million in cash to Justin Sun, the founder of blockchain-focused startup TRON. TRON is a decentralized entertainment and content-sharing platform that uses blockchain and distributed storage technology. It allows users to publish content without […]
Alerte au sujet de faux mails promettant un remboursement de l’assurance-maladie
Les messages frauduleux demandent à leurs destinataires de transmettre des coordonnées bancaires, ce que ne fait jamais la véritable assurance-maladie. La nouvelle est trop belle pour être vraie : cybermalveillance.gouv.fr, organe gouvernemental notamment chargé de prévenir des arnaques sur internet, a alerté sur de faux mails de l’assurance-maladie, lundi 11 juin. Ces messages affirment à […]
Ex-CIA Employee Charged with Leak of Classified CIA Vault 7 Hacking Tools
The Department of Justice has announced new charges against former CIA software engineer Joshua Schulte for allegedly leaking classified CIA documents, software projects, and hacking utilities called Vault 7 to WikiLeaks. Schulte was charged on August 24, 2017 with possession of child pornography, but was also believed to be the source of the embarrassing […]
Hacking more than 400 Axis camera models by chaining 3 flaws
Researchers from cybersecurity firm VDOO have discovered several vulnerabilities affecting nearly 400 security cameras from Axis Communications. Researchers from cybersecurity firm VDOO have conducted a study on IoT devices and discovered seven vulnerabilities in cameras manufactured by Axis Communications. According to the vendor, nearly 400 models are affected by the […]
DHS, FBI published a join alert including technical details of Hidden Cobra-linked ‘Typeframe’ Malware
The US DHS and the FBI have published a new joint report that includes technical details of a piece of malware allegedly used by the Hidden Cobra APT. A new joint report published by US DHS and FBI made the headlines, past document details TTPs associated with North Korea-linked threat groups, tracked […]