Called BleedingBit, this vulnerability impacts wireless networks used in a large percentage of enterprise companies. Two zero-day vulnerabilities in Bluetooth Low-Energy chips made by Texas Instruments (and used in millions of wireless access points) open corporate networks to crippling stealth attacks. Adversaries can exploit the bugs by simply being approximately […]
Haythem Elmir
PoC Exploit Compromises Microsoft Live Accounts via Subdomain Hijacking
Poor DNS housekeeping opens the door to account takeover. A proof-of-concept (PoC) attack details how an attacker can gain access a victim’s Microsoft Live webmail session, without having the person’s credentials. It relies upon the hijack of a Microsoft-owned Live.com website subdomain. The PoC, developed by CyberInt, demonstrates what it […]
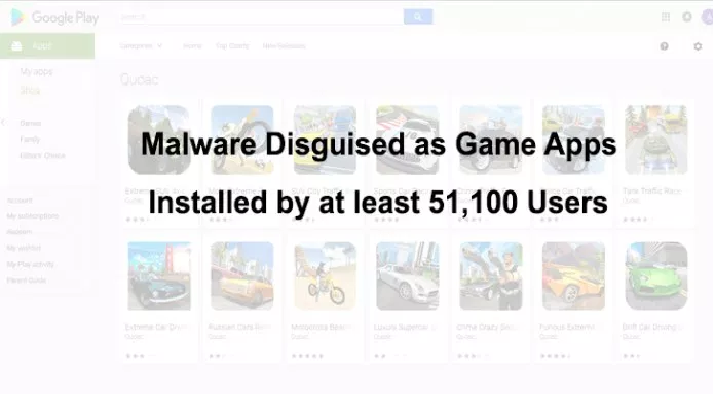
Beware! Downloader Malware Disguised as Game Apps Found On Google Play with More Than 51,100 Installations
The downloader malware dubbed Android.DownLoader.819.origin malware found on Google play downloaded by more than 51,100 Android users. The downloader malware is capable of installing other malicious applications on the affected devices and launches them. Doctor Web security researchers found 14 copies of the malicious application distributed by Quoac developer disguised as […]
BLEEDINGBIT Bluetooth flaws in TI chips expose enterprises to remote attacks
Two vulnerabilities in new Bluetooth chip, dubbed BLEEDINGBIT expose millions of access points and other networking devices to remote attacks. Security experts from the IoT security firm Armis, the same that found the BlueBorne Bluetooth flaws, have discovered two serious vulnerabilities in BLE chips designed by Texas Instruments. The flaws, dubbed BLEEDINGBIT by Armis, could be exploited by a […]
Iran hit by a more aggressive and sophisticated Stuxnet version
Iran’s strategic network was hit by a new destructive and sophisticated version of the Stuxnet cyber weapon, the Hadashot TV reports. According to the Hadashot TV, Iran’s strategic network was hit by a destructive malware-based attack hours after Israel revealed the Mossad had thwarted an Iranian murder plot in Denmark, and days after Iran’s […]
Emotet Awakens With New Campaign of Mass Email Exfiltration
The Emotet malware family just raised the stakes by adding email exfiltration to its arsenal, thereby escalating its capabilities to cyber espionage. While it has recently made headlines for delivering ransomware payloads to United States infrastructure such as Water Utilities, Emotet has laid mostly dormant for the past month. In […]
Now use Internet anonymously through Tor-enabled SIM card Onion3G
Now use Internet anonymously through Tor-enabled SIM card Onion3G Privacy concerns are rising with the advancement of technology. Today, we need to be a lot more careful about online browsing than we needed to a few years back despite that we have come far ahead with technology. Tor browser and VPNs are generally […]
Cisco Warns of Zero-Day Vulnerability in Security Appliances
Cisco informed customers on Wednesday that some of its security appliances are affected by a serious vulnerability that has been actively exploited. The zero-day flaw, tracked as CVE-2018-15454, is related to the Session Initiation Protocol (SIP) inspection engine used in the company’s Adaptive Security Appliance (ASA) and Firepower Threat Defense […]
Cyber Criminals attacked the system of Russian Railways and S7 airlines and killed the investigator
The court of Moscow began consideration of the case of fraud in the purchase of tickets. A group of hackers, consisting of 29 people, earned $ 258,000 on fictitious refunds of tickets of Russian Railways and S7 airlines in 2013-2014. This case was conducted by Evgenija Shishkina, the senior investigator […]
Kraken Ransomware Upgrades Distribution with RaaS Model
Affiliates pocket 80 percent of every ransom payment. The Kraken ransomware author has released a second version of the malicious code, along with a unique affiliate program on the Dark Web. According to research into Kraken v.2 the new version is being promoted in a ransomware-as-a-service (RaaS) model to underground […]