The McAfee Mobile Research team recently examined a new threat, Android malware that contains a backdoor file in the executable and linkable format (ELF). The ELF file is similar to several executables that have been reported to belong to the Lazarus cybercrime group. (For more on Lazarus, read this post from our Advanced Threat Research Team.)
The malware poses as a legitimate APK, available from Google Play, for reading the Bible in Korean. The legit app has been installed more than 1,300 times. The malware has never appeared on Google Play, and we do not know how the repackaged APK is spread in the wild.

Figure 1: Description of the legitimate app on Google Play.
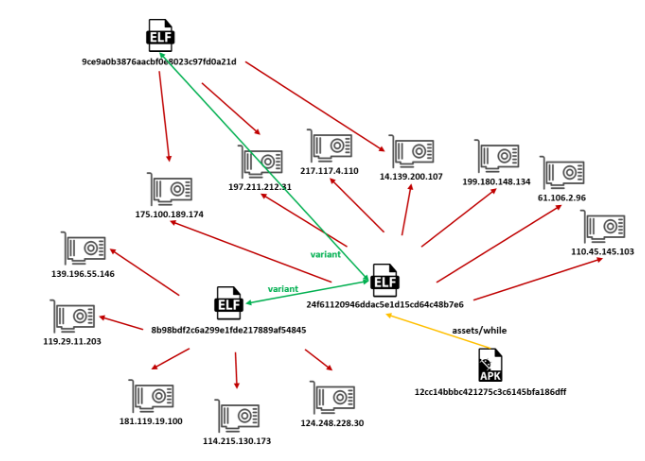 Figure 2: An overview of the malware’s operation.
Figure 2: An overview of the malware’s operation.
Comparing Certificates
The repackaged APK has been signed by a different certificate from the legitimate APK. We can see the differences in the following two screen captures:![]()
Figure 3: The certificate of the malicious, repackaged APK.
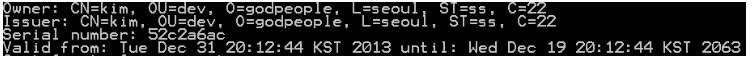
Figure 4: The certificate of the legitimate APK.
To read the original article:
https://securingtomorrow.mcafee.com/mcafee-labs/android-malware-appears-linked-to-lazarus-cybercrime-group/#sf173817982
