The Mirai Botnet Is Attacking Again…
And the spinoff bots – and all their command and control hostnames buried in the morass of digital data – are hilarious.
The Mirai botnet is kind of like Madonna. They both were huge once. Then the adoring public shifted their attention to younger, newer acts, but they keep on performing anyway. We wrote about Mirai extensively after we predicted its construction in our first IoT report, DDoS’s Newest Minions: IoT Devices in 2016.
Mirai has been in the news again recently. In December, Brian Krebs reported that two men pleaded guilty as the co-authors of the IoT botnet. A new botnet, Satori (Japanese for « the awakening ») is a possible successor to Mirai. The source code for Satori was recently posted to Pastebin as a Christmas gift to the IoT hacker community. Like Reaper, Satori weaponizes exploits beyond simple brute-force default password guessing.
F5 Labs and our data partner, Loryka, still monitor Mirai (but not Madonna!). Even though Satori and Reaper might be the interesting new acts, Mirai and its children are still actively attacking from the Internet of Things. Our honeypots grab configurations from each botnet and we compile the list of command and control (C&C, aka C2 or CNC) hostnames that are used to control each bot. Attacks from the C&C host themselves are rare, but they make good indicators of compromise (IOC) because any requests for those hosts from inside a protected network can be traced back to the infected devices themselves.
So, we were looking through last quarter’s list of Mirai spinoff bots and all of their command and control hostnames and had a bit of a laugh. Of course, we take this botnet stuff seriously, but we couldn’t help snickering a little at some of the domain names.
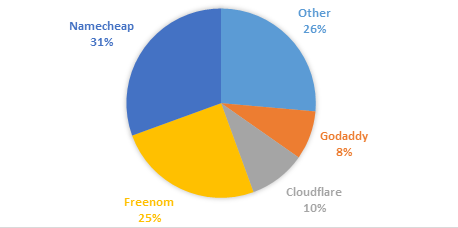
Of the 203 C&C hostnames we sampled in the last quarter of 2017, about 70 are still active in DNS. And of that original 203, 71% were registered (and almost certainly hosted) by Freenom, Namecheap (an Enom reseller), or Cloudflare. If you were a cybercriminal, why not use « free » domain registration services like Freenom for your C&C hosts? A simple Google search will tell you they care little about what you do with the domain as long as you use it (or they will eagerly park your domain and start collecting ad revenue).
When it comes to domain registrars like Enom that offer reseller services to companies like Namecheap, the layers of domain management and orchestration from the registrant to the controller can make it harder to track down and process abuse complaints. Because cyber criminals know this, they often favor resellers instead of direct registrars. A simple Google search for Namecheap will turn up a history of complaints alleging they do little about abuse complaints, so it’s not surprising cybercriminals would chose to use them. Cloudflare, on the other hand, has drawn fire from Brian Krebs for their continued hosting of obvious DDoS-for-hire services.
Sure, the C&C list is a small sample size, and C&C hosts come and go quickly. This list is in no way exhaustive — it’s just a snapshot in time from last quarter. But for a breakdown of the domain hosting services, see the end of this article.
To read the original article
https://www.darkreading.com/partner-perspectives/f5/the-mirai-botnet-is-attacking-again/a/d-id/1331031