Reminiscent of the old « Effective Power » bug that has long caused iMessage apps to crash on iOS devices, a new bug nicknamed chaiOS has surfaced this week with similar repercussions.
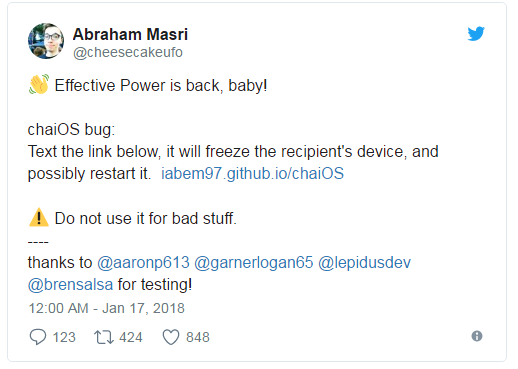
Discovered by Abraham Masri, the chaiOS bug is another « text bomb » that when sent to other users will crash that person’s iMessage application in a continuous loop.
Bug affects both iOS and macOS
Experts have not pinpointed the exact cause of the chaiOS bug just yet, but unlike Effective Power, chaiOS also works on macOS, not just iOS devices. According to the experts at Yalu Jailbreak, the bug affects iMessage apps on macOS High Sierra, iOS 10 to 10.3.3, and iOS 11 to 11.2.1.
All users have to do is send a link to a web page hosting a piece of JavaScript code that attempts to send an SMS message.
This sounds pretty benign, but Apple’s iMessage application somehow fails so miserably when handling this code that the app crashes and sometimes enters a reboot loop.
Bug primed to be abused for pranks and nothing else
A proof-of-concept page has been put together by Masri and shared on Twitter yesterday, but the page has been taken down by GitHub fearing abuse.
That didn’t stop other users from creating several clones and hosting these pages on private servers. Right now, the bug does not look to be anything more than another way to prank Apple users.
We recommend our readers to exert caution when sending such links to friends that may be using their device for crucial tasks. One of these pranks had gone terribly wrong in the past when a similar link shared on Twitter crashed 911 services in a few Arizona emergency centers, resulting in criminal charges against a 19-year-old man named Meetkumar Hiteshbhai Desai.
To read the original article:https://www.bleepingcomputer.com/news/apple/chaios-text-bomb-crashes-imessage-app-on-macos-and-ios/
