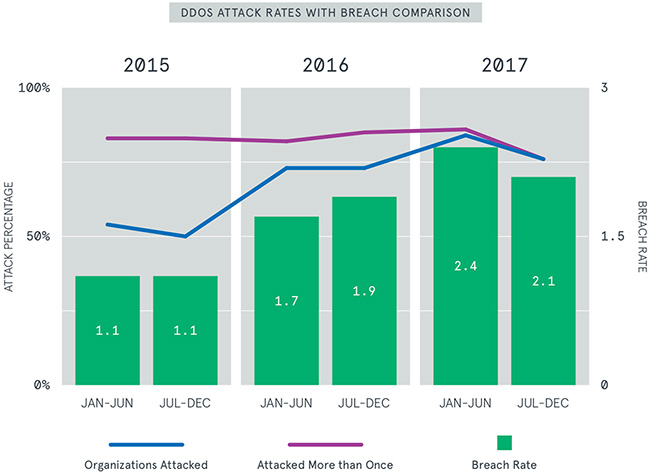
DDoS attacks continue to be an effective means to distract and confuse security teams while inflicting serious damage on brands. Neustar discovered that brands experienced a 27 percent increase in the number of breaches per DDoS attack, despite suffering similar attack levels in the same time period last year.
Attackers are getting higher yields from determined attacks
Data from the report shows attackers are achieving higher levels of success against brands they only hit once: 52 percent of brands reported a virus associated with a DDoS attack, 35 percent reported malware, 21 percent reported ransomware and 18 percent reported lost customer data.
Over a twelve-month period, 75 percent of respondents recorded multiple DDoS attack attempts following an initial assault on their brand’s network. The resulting breach ratio increases as the number of DDoS attacks increases, but the net result is it only takes one attack to breach a brand’s defenses.
Findings suggest that cybercriminals are focused on taunting defenses, probing network vulnerabilities and executing more targeted strikes, instead of making noise with a singular, large attack.
“Not only are hackers becoming craftier and more dangerous, but they’re also becoming more opportunistic,” said Nicolai Bezsonoff, Vice President, Neustar Security Solutions. “The importance of always-on vigilance and investment in DDoS security technology is essential for brands looking to adapt and evolve their defenses. Protecting a brand’s infrastructure and customer data against threats is paramount in the current digital landscape.”
To read the original article:
https://www.helpnetsecurity.com/2017/10/12/ddos-attacks-brands/
