Two things happened on Halloween with a bearing on cybersecurity. The first is that the 15th year of the National Cyber Security Awareness Month (NCSAM) came to an end. You have heard of NCSAM, right? The second, apparently timed to coincide with 31 October, was that Google is yet again modifying the background security […]
Année : 2018
Cyberattaques contre les agences de voyage
Cyberattaques contre les agences de voyage: la FTAV et Amadeus en campagne de sensibilisation 111 billets d’avion pour une valeur de 350 MD émis frauduleusement par des hackers sur le dos des agences de voyage tunisiennes entre 2011 et 2018. C’est le constat amer fait par Amadeus Tunisie, principal GDS fournisseur de solutions technologiques […]
Méfiez-vous de cette arnaque très sophistiquée !
Une opération d’hameçonnage (phishing en anglais) a touché ces derniers jours un grand nombre d’utilisateurs des services de messagerie sous la forme d’un mail envoyé par un contact qui vous conseille de changer immédiatement votre mot de passe au motif qu’ il a été piraté par des hackers. Une manipulation […]
Russian hackers compromise 120 million Facebook accounts; private messages on sale online
Facebook has fallen victim to countless security breaches and November brings even more bad news for the social network. Russian hackers are selling private conversations of at least 81,000 Facebook accounts at 10 cents per account, writes the BBC. According to the BBC Russian Service, which communicated with the hackers, the criminals […]
Two Zero-Day Bugs Open Millions of Wireless Access Points to Attack
Called BleedingBit, this vulnerability impacts wireless networks used in a large percentage of enterprise companies. Two zero-day vulnerabilities in Bluetooth Low-Energy chips made by Texas Instruments (and used in millions of wireless access points) open corporate networks to crippling stealth attacks. Adversaries can exploit the bugs by simply being approximately […]
PoC Exploit Compromises Microsoft Live Accounts via Subdomain Hijacking
Poor DNS housekeeping opens the door to account takeover. A proof-of-concept (PoC) attack details how an attacker can gain access a victim’s Microsoft Live webmail session, without having the person’s credentials. It relies upon the hijack of a Microsoft-owned Live.com website subdomain. The PoC, developed by CyberInt, demonstrates what it […]
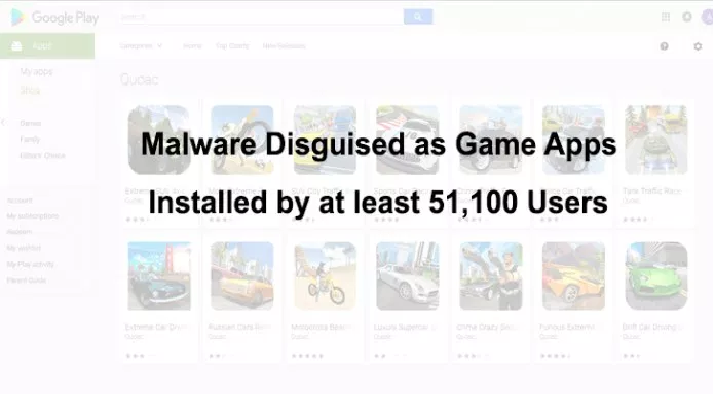
Beware! Downloader Malware Disguised as Game Apps Found On Google Play with More Than 51,100 Installations
The downloader malware dubbed Android.DownLoader.819.origin malware found on Google play downloaded by more than 51,100 Android users. The downloader malware is capable of installing other malicious applications on the affected devices and launches them. Doctor Web security researchers found 14 copies of the malicious application distributed by Quoac developer disguised as […]
BLEEDINGBIT Bluetooth flaws in TI chips expose enterprises to remote attacks
Two vulnerabilities in new Bluetooth chip, dubbed BLEEDINGBIT expose millions of access points and other networking devices to remote attacks. Security experts from the IoT security firm Armis, the same that found the BlueBorne Bluetooth flaws, have discovered two serious vulnerabilities in BLE chips designed by Texas Instruments. The flaws, dubbed BLEEDINGBIT by Armis, could be exploited by a […]
Iran hit by a more aggressive and sophisticated Stuxnet version
Iran’s strategic network was hit by a new destructive and sophisticated version of the Stuxnet cyber weapon, the Hadashot TV reports. According to the Hadashot TV, Iran’s strategic network was hit by a destructive malware-based attack hours after Israel revealed the Mossad had thwarted an Iranian murder plot in Denmark, and days after Iran’s […]
Emotet Awakens With New Campaign of Mass Email Exfiltration
The Emotet malware family just raised the stakes by adding email exfiltration to its arsenal, thereby escalating its capabilities to cyber espionage. While it has recently made headlines for delivering ransomware payloads to United States infrastructure such as Water Utilities, Emotet has laid mostly dormant for the past month. In […]