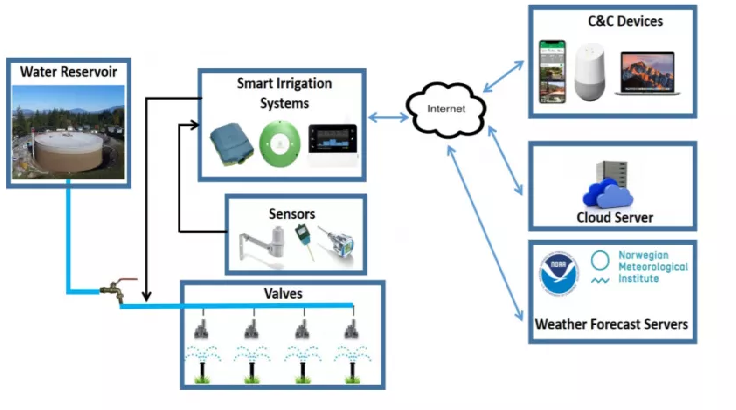
Piping botnet – Israeli researchers warn of a potential distributed attack against urban water services that uses a botnet of smart irrigation systems that water simultaneously. Ben-Gurion University of the Negev (BGU) cyber security researchers warn of a potential distributed attack against urban water services that uses a botnet of […]
Année : 2018
Cosmos Bank’s server Hacked: Hackers Stolen Around Rs 94 Crore On Two Separate Days
Hackers compromised the Cosmos Bank server and allegedly transferred over Rs 94 crore between August 11 and August 13. The Cosmos Bank is the oldest and second largest bank in India, it was established in 1906. According to the bank statement, hackers propagated malware to one the ATM Switch servers […]
KeyPass ransomware
In the last few days, our anti-ransomware module has been detecting a new variant of malware – KeyPass ransomware. Others in the security community have also noticed that this ransomware began to actively spread in August: Notification from MalwareHunterTeam Distribution model According to our information, the malware is propagated by means of […]
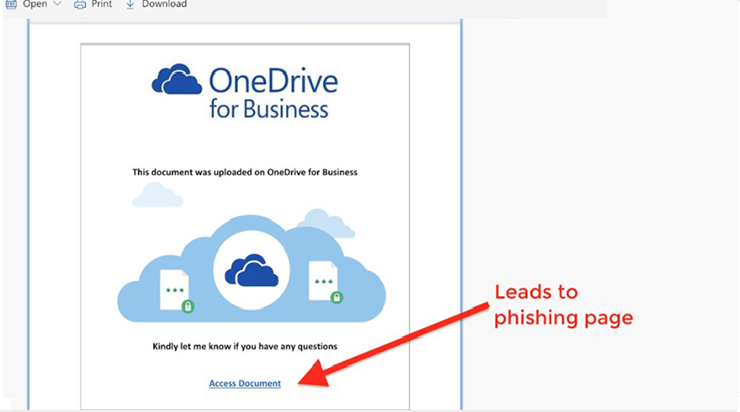
New Office 365 phishing attack uses malicious links in SharePoint documents
Fake emails targeting Office 365 users via malicious links inserted into SharePoint documents are the latest trick phishers employ to bypass the platform’s built-in security, Avanan researchers warn. The cloud security company says that the phishing attack was leveraged against some 10% of its Office 365 customers in the past […]
L1 Terminal Fault (L1TF) ou « Foreshadow », une vulnérabilité concerne les processeurs intel
Dans le cadre de notre partenariat avec Intel, nous avons été informés de la découverte d’un vecteur exploitant les failles de type « attaques par canal auxiliaire d’exécution spéculative » (speculative execution side-channel attaks). Cette nouvelle vulnérabilité, L1 Terminal Fault (L1TF), ou Foreshadow, est donc apparentée aux failles Spectre et Meltdown dévoilées […]
Btlejacking Attack Could Allow a Hacker to Jam and Takeover the Bluetooth Connection
The Btlejacking Attack allows taking control over any Bluetooth Low Energy device, the attack abuses supervision timeout between two connected devices. The supervision timeout defines the time after which the connection is if no valid packets have been received. Security researcher Damien Cauquil reveal the attack on Aug. 11 Defcon hacker conference […]
World’s Largest Web Hoster GoDaddy Exposed Massive Amount Of Sensitive Data Online
GoDaddy data leaked from an unsecured S3 bucket, exposed the data contains configuration information such as hostname, operating system, workload, AWS region, memory and CPU specs, and more. Godaddy is the world’s leading domain registrar with over 18 million customers with over 76M domain names. Upguard noticed the publically readable […]
Vulnerabilities in Fax Protocol Let Hackers Infiltrate Networks via Fax Machines
Two recently discovered vulnerabilities in the fax protocol can transform fax machines into entry points for hackers into corporate networks, two Check Point researchers revealed last week in a talk given at the DEF CON 26 security conference held in Las Vegas. Named « Faxploit, » this attack targets the ITU T.30 […]
Infamous Belarusian Hacker « Ar3s » behind Massive Andromeda Botnet Released
Sergei Yaretz, 35-year-old, one of the most wanted hackers from Belarus who was arrested in last December has been released. It is reported that this is the first time in Belarus there was a process of cyber crime. In December 2017, Sergei also known as ‘Ar3s'( ‘Арес’ in Russian/Ares – The […]
Hacker leaks Snapchat’s source code on Github
Pakistani Hacker Posted Authentic Snapchat Source Code on GitHub – Snapchat’s source code is stolen…can there be a bigger news than that? Perhaps there is! Not only that the source code has been stolen but also posted on Microsoft-owned GitHub of all the platforms. Reportedly, the hacker hails from a small village […]