Ad targeters are exploiting browsers’ built-in login managers to covertly collect hashes of users’ email addresses, to be used to track them across the web. “Email addresses are unique and persistent, and thus the hash of an email address is an excellent tracking identifier,” Princeton University’s Center for Information Technology […]
Année : 2018
AMD Soars After Rival Intel Reveals Processor Flaw
According to technology website The Register, Intel has a bug that lets some software gain access to parts of a computer’s memory that are set aside to protect things like passwords. All computers with Intel chips from the past 10 years appear to be affected, the report said, and […]
How to keep your browser and devices safe from cryptojackers
Stealthy cryptocurrency mining scripts have found their way to a variety of websites – streaming, gaming, online stores, and so on. The craze started with CoinHive, but copycats have soon started popping up and increasing the probability for users to get their browsers hijacked into mining crypto currency (mostly Monero). […]
Upcoming patches for security flaw in Intel processors expected to slow down computers
Windows users whose PCs run on Intel processors can apparently expect their computers to slow down after next Tuesday. In fact, all computers using modern Intel chips – whether they run Windows, Linux or macOS – are expected to suffer a performance hit in the coming days. The reason for […]
Obsolescence Programmée et fraudes : Apple et Epson dans le viseur de la DGCCRF
Des réclamations de consommateurs déposées par HOP le 18 septembre dernier ont été entendues par le parquet de Nanterre, et ont mené à l’ouverture d’une enquête contre le fabricant américain d’imprimantes Epson, rapporte Euractiv relayant un article du JDLE. Obsolescence programmée, c’est le sujet de l’enquête. Dans le menu, fausse […]
VMWARE ISSUES 3 CRITICAL PATCHES FOR VSPHERE DATA PROTECTION
VMware, a Dell Technologies subsidiary, released several patches Tuesday fixing critical vulnerabilities affecting its vSphere cloud computing virtualization platform. The bugs address three vulnerabilities in VMware’s vSphere Data Protection (VDP), a backup and recovery solution used with its vSphere platform. According to the company, a remote attacker could exploit the […]
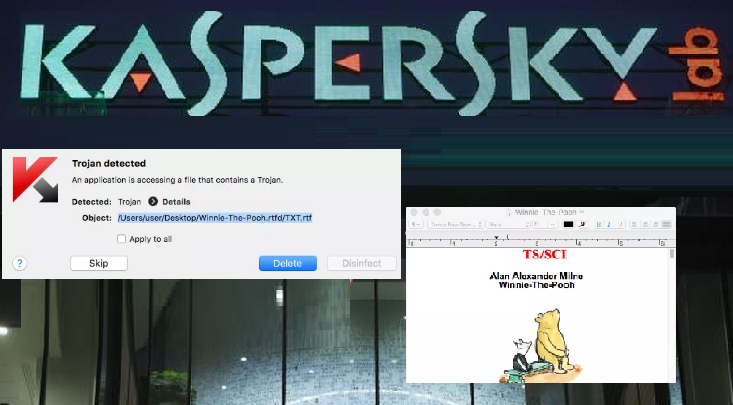
Former NSA hacker reversed Kaspersky Lab antivirus to compose signatures capable of detecting classified documents
Former NSA hacker, demonstrated how to subvert the Kaspersky Lab antivirus and turn it into a powerful search tool for classified documents. The Kaspersky case demonstrated that security software can be exploited by intelligence agencies as a powerful spy tool. Patrick Wardle, chief research officer at Digita Security and former NSA […]
Necurs botnet involved in massive ransomware campaigns at the end of 2017
The Necurs botnet made the headlines at year-end sending out tens of millions of spam emails daily as part of massive ransomware campaigns. Necurs was not active for a long period at the beginning of 2017 and resumed it activity in April. The Necurs botnet was used in the past months to push […]
MACOS LPE EXPLOIT GIVES ATTACKERS ROOT ACCESS
A researcher that goes by the handle “Siguza” released details of a local privilege escalation attack against macOS that dates back to 2002. A successful attack could give adversaries complete root access to targeted systems. Siguza released details of the attack on Dec. 31 via Twitter, wishing followers a “Happy […]
Critical Flaw Reported In phpMyAdmin Lets Attackers Damage Databases
A critical security vulnerability has been reported in phpMyAdmin—one of the most popular applications for managing the MySQL database—which could allow remote attackers to perform dangerous database operations just by tricking administrators into clicking a link. Discovered by an Indian security researcher, Ashutosh Barot, the vulnerability is a cross-site request […]