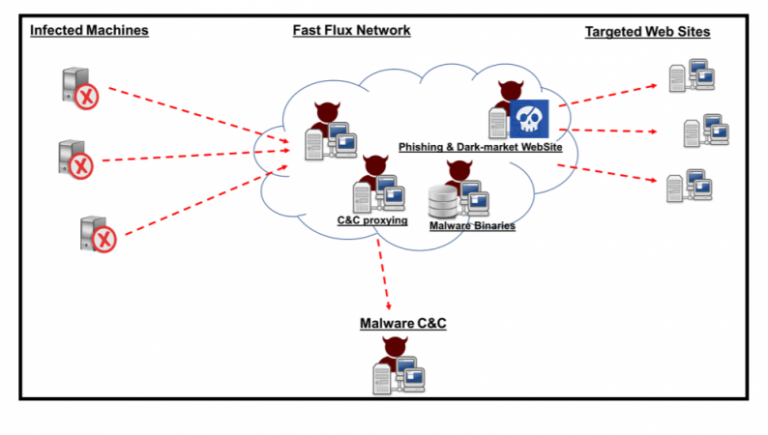
xperts at Akamai have identified a running Fast Flux botnet composed of over 14,000 compromised systems used to spread malware. Experts at Akamai have identified a running botnet of over 14,000 compromised systems used to spread malware. The botmasters implemented a technique dubbed Fast Flux to make the infrastructure hard […]
Scam Alert: Your Trusted Friends Can Hack Your Facebook Account
If you receive a message from any of your Facebook Friends asking for urgent help to recover their Facebook account, since they’ve added you as one of their ‘Trusted Contacts‘—just don’t blindly believe it. Researchers have detected a new Facebook phishing scam that can even trick an experienced technical user […]
Précisions à propos des perturbations sur Yahoo Mail
Suite à ce qu’à été publié sur quelques sites électroniques à propos des perturbations constatées sur le portail web mail de Yahoo, l’ATI tient à préciser ce qui suit : 1-Tous les serveurs DNS Tunisiens y compris les serveurs de l’ATI sont opérationnels d’une manière continue et sans arrêt. Leurs […]
LOCKY GETS UPDATED TO ‘YKCOL’, PART OF RAPID-FIRE SPAM CAMPAIGNS
Cybercriminals behind the Locky ransomware have revamped the malware’s code three times in 30-day period and blasted out massive spam campaigns. According to researchers at Trustwave, the latest variant of Locky ransomware is called Ykcol (that’s Locky spelled backwards) and was part of a Sept. 19 spam blast targeting 3 […]
Surveillance d’Internet: les solutions pour protéger sa navigation.
Tout ce qui passe par Internet peut être intercepté, écouté et stocké ailleurs. Les emails que vous envoyez, les dossiers que vous partagez, les photos que vous publiez en ligne…. Et par qui? Si on ne va pas non plus tomber dans la paranoïa totale, beaucoup de monde peut y […]
Hackers were able to steal $60 million from Taiwanese bank.
Last week, a hacking group was able to abuse the SWIFT (the Society for Worldwide Interbank Financial Telecommunications) banking network to steal $60 million after installing malware on a Taiwanese bank’s servers. The Far Eastern International Bank has admitted that malware had been found on its machine systems, affecting PCs […]
iOS Flaw Makes Apple ID Passwords Prone to Phishing Attacks
According to the findings of Felix Krause, a mobile app developer and founder of Fastlane, there is a flaw in iOS that is potentially dangerous for the security of users’ passwords. In his blog post, Krause explained that cybercriminals could use pop-up dialog boxes to carry out phishing attacks so that an unsuspecting user could be […]
Unpatched SQLi vulnerability in SmartVista e-commerce suite
Companies using SmartVista, the popular e-commerce/payment management product suite developed by Swiss company BPC Banking Technologies, are urged to put limit access to its management interface. That’s because Rapid7 researcher Aaron Herndon found a SQL injection vulnerability in it, and BPC has shown no indication that it’s going to fix […]
SEC spoofed, malware hosted on US gov’t server in new DNS attack
Researchers have discovered a new version of the DNS Messenger attack which masquerades as the US Securities and Exchange Commission (SEC) and hosts malware on compromised government servers. On Wednesday, security researches from Cisco Talos revealed the results of an investigation into DNS Messenger, a fileless attack which uses DNS […]
DDoS attacks: Brands have plenty to lose, even if attacked only once
DDoS attacks continue to be an effective means to distract and confuse security teams while inflicting serious damage on brands. Neustar discovered that brands experienced a 27 percent increase in the number of breaches per DDoS attack, despite suffering similar attack levels in the same time period last year. Attackers […]