A critical vulnerability affects hundreds of thousands of email servers. A fix has been released but this flaw affects more than half of the Internet’s email servers, and patching the issue will take weeks if not months. The bug is a vulnerability in Exim, a mail transfer agent (MTA) —software that […]
World’s largest DDoS attack record broken by a new memcached DDoS attack
World’s largest DDoS attack record lasted just a few days, Arbor Networks reported that earlier this month a US service provider suffered a 1.7Tbps memcached DDoS attack. On February 28, 2018, the code hosting website GitHub was hit by the largest-ever DDoS attack that peaked at 1.3Tbps. The powerful attack was abusing the […]
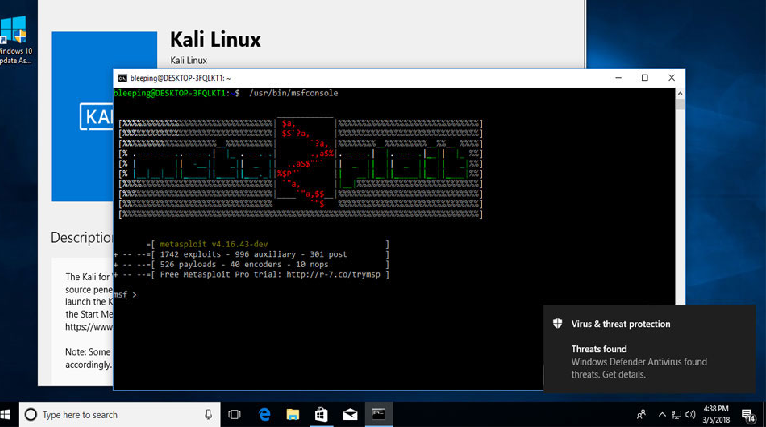
Kali Linux Now in Windows Store, but Defender Flags Its Packages as Threats!
The penetration testing and security auditing platform called Kali Linux is now available in the Windows 10 Store as a Linux environment that can be used with the Windows Subsystem for Linux (WSL). The problem is someone forgot one little thing. Some of Kali’s more popular packages are detected as hacktools and exploits […]
600 Powerful Bitcoin-Mining Computers Worth $2 Million Stolen In Iceland
Around 600 powerful devices specifically designed for mining bitcoin and other cryptocurrencies have been stolen from Icelandic data centers in what has been dubbed the « Big Bitcoin Heist. » To make a profit, so far criminals have hacked cryptocurrency exchanges, spread mining malware, and ransomware—and even kidnapped cryptocurrency investors for ransom and tried to rob a bitcoin […]
How to bypass authentication on Windows Server 2008 R2
In this article we will be looking at how easy it is to bypass authentication and reset the administrator password on a Windows Server 2008 R2 installation. This technique requires us to have physical access to the machine that is running the Windows server or have access to the management interface of the hypervisor when […]
The newest attack for stealing network data!
Israeli cyber security expert reveals the newest attack for stealing network data. Security researchers at the Ben-Gurion University of the Negev (BGU) found that attackers can secretly obtain data (such as encryption keys, passwords and files) from extremely secure or air-gapped networks via the row of status LEDs that exists in […]
New attacks on 4G LTE networks can allow to spy on users and spoof emergency alerts
A group of researchers discovered a number of weaknesses in the 4G LTE networks that could be exploited by attackers to eavesdrop on phone calls and text messages, knock devices offline, track location, and spoof emergency alerts. A group of researchers from Purdue and the University of Iowa have discovered a […]
Windows Defender ATP Detects Spyware Used by Law Enforcement: Microsoft
Microsoft Dissects FinFisher’s Complex Infection Process Windows Defender Advanced Threat Protection (Windows Defender ATP) is capable of detecting behavior associated with the sophisticated FinFisher spyware, Microsoft says, after performing an in-depth analysis of the malware’s infection process. FinFisher is a lawful interception solution built by Germany-based FinFisher GmbH, which sells […]
Payment Card Breach Hits Some Applebee’s Restaurants
RMH Franchise Holdings revealed on Friday that malware had been found on point-of-sale (PoS) systems at the Applebee’s restaurants it operates as a franchise. RMH disclosed the incident on Friday afternoon, which often indicates an attempt to avoid the news cycle and fly under the radar. The company posted a […]
US Air Force Hacked for Good at HackerOne’s Bug Bounty Event
106 Security Flaws Identified in Operationally Significant DoD Websites under US Air Force’s Bug Bounty Challenge. A team of white hat hackers working with HackerOne, a vulnerability coordination and bug bounty platform hosted a bug bounty event in collaboration with the US Air Force to identify bugs and security vulnerabilities […]