For at past nine years, Mozilla has been using an insufficiently strong encryption mechanism for the « master password » feature.
Both Firefox and Thunderbird allow users to set up a « master password » through their settings panel. This master password plays the role of an encryption key that is used to encrypt each password string the user saves in his browser or email client.
Experts have lauded the feature because up until that point browsers would store passwords locally in cleartext, leaving them vulnerable to malware or attackers with physical access to a victim’s computer.
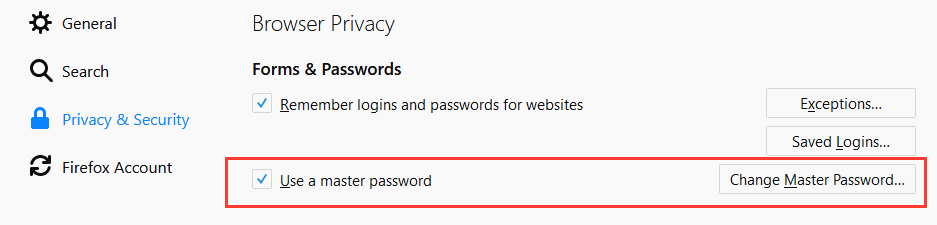
But Wladimir Palant, the author of the AdBlock Plus extension, says the encryption scheme used by the master password feature is weak and can be easily brute-forced.
Master password encryption uses low SHA1 iteration count
« I looked into the source code, » Palant says, « I eventually found the sftkdb_passwordToKey() function that converts a [website] password into an encryption key by means of applying SHA-1 hashing to a string consisting of a random salt and your actual master password. »
« Anybody who ever designed a login function on a website will likely see the red flag here, » Palant says.
The flag Palant is referring to is the fact that the SHA-1 function has an iteration count of 1, meaning it’s applied just once, while industry practices regard 10,000 as a solid minimum for this value, while applications like LastPass use values of 100,000.
This low iteration count makes it incredibly easy for an attacker to brute-force the master password and later decrypt the encrypted passwords stored inside the Firefox or Thunderbird databases.
Palant points to recent advances in GPU card technologies that now allow attackers to brute-force simplistic master passwords in under a minute.
Issue first reported nine years ago
But Palant wasn’t the first to notice such weakness. A Mozilla bug tracker entry by Justin Dolske from nine years ago reported the same issue, soon after the master password feature’s launch.
Dolske also pointed to the low iteration count of 1 as the master password’s main problem. But despite the report, Mozilla did not take any official action for years.
It was only until this past week when Palant reanimated the original bug report that Mozilla finally provided an official answer, suggesting this would be fixed with the launch of Firefox’s new password manager component —currently codenamed Lockbox and available as an extension.
Using a master password is much better than the alternative of not using one. For the time being, choosing longer and more complex master passwords mitigates the feature’s inherent weak encryption scheme. Users who want to be sure nobody can touch their web passwords should use a third-party password manager application.
The optimum solution, according to Palant, would be if Mozilla engineers would employ the Argon2 library for hashing passwords instead of SHA1.
To read the original article:
