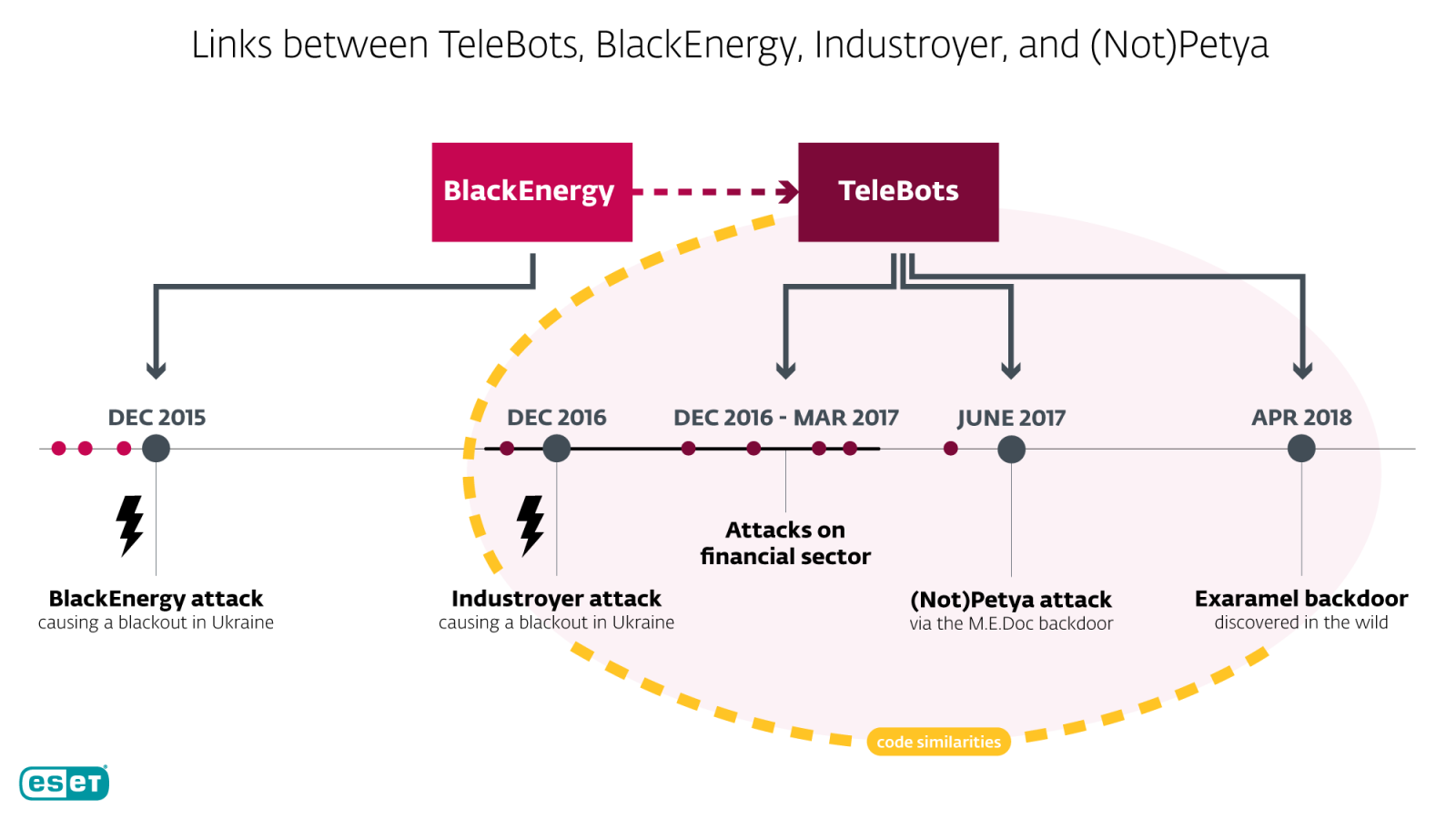
Security researchers found the missing link that helps them prove that the NotPetya disk-wiping malware and the Industroyer backdoor for electric power systems are the work of the TeleBots group.
Both pieces of malware were used in attacks against targets in Ukraine and researchers have found clues in the past pointing to the same actor being behind them, but could confirm this only with « low confidence. »
In a report today shared in advance with BleepingComputer, ESET reveals that the link between the two pieces of malware is a new backdoor deployed by TeleBots as the successor for the main Industroyer variant.
Previously, researchers from ESET and Kaspersky relied on the discovery of shared infrastructure and TTPs (Tactics, Techniques, and Procedures) to support their theory; these do not represent reliable evidence because they can be abandoned over time and picked by a different threat actor.
Code comparison points to the same author
This time, evidence comes from technical indicators such as code similarities, shared infrastructure for command and control (C2) servers and malware execution routine. Code and behavior of the malicious tools show that the same author is behind them, even if they are used by a different adversary in time.
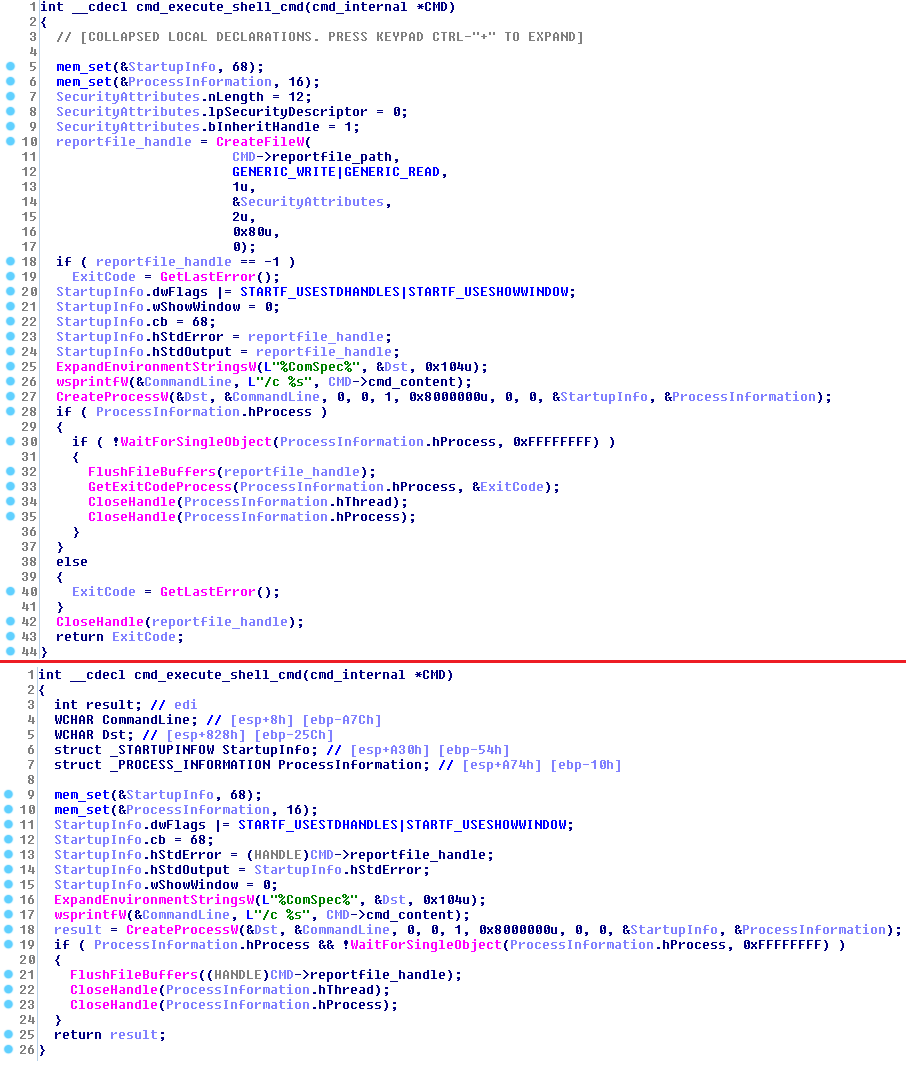
« Both [Exaramel and Industroyer] use a report file for storing the result output of executed shell commands and launched processes, » notes the report from ESET.
Furthermore, the two malware variants share code similarities and behavior that ties them to the same author.
« The code of the command loop and implementations of the first six commands are very similar to those found in a backdoor used in the Industroyer toolset, » ESET researchers say.
TeleBots’ impressive arsenal
TeleBots group has been associated with multiple malware families in the past including the BlackEnergy toolkit responsible for the power blackout in Ukraine in 2015; NotPetya – the fake ransomware that caused massive operational disruptions and financial damage at companies around the globe.
Industroyer is also attributed to TeleBots, who used it to cause the 2016 power outage in Ukraine; it is a backdoor specifically designed to disrupt the working processes in industrial control systems, electrical substations in particular.
Exaramel completes the assortment of malicious tools used by TeleBots in Ukraine. ESET says that it was used against an organization that is not an industrial facility. It is also linking the TeleBot tools, painting a better picture of this actor’s capabilities.
To read the original article
