Security researchers at NetLab, a sub-division of the Chinese cybersecurity firm Qihoo 360, have discovered a new, wide-scale, and very active malware campaign that has managed to hijack more than 100,000 home routers between Sept 21 and 27. A majority of routers (almost 88%) are located in Brazil.
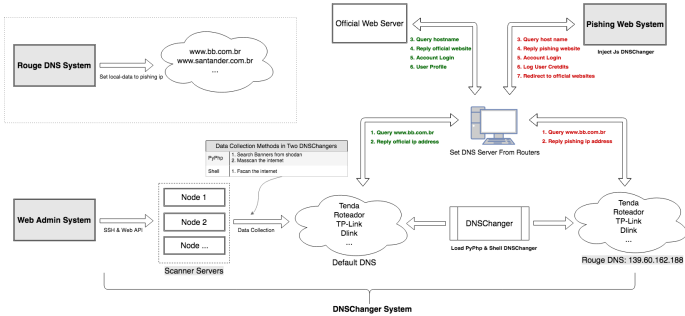
The malware has been dubbed GhostDNS. Once a router is hijacked, the malware modifies its DNS settings to upload malicious web pages and steal user data such as login credentials for banking sites. The campaign shares stark similarities with an infamous malware DNSChanger, which also used to modify DNS server settings after infecting a device to let attackers route the internet traffic via infected servers to steal sensitive data.
GhostDNS scans for IP addresses for routers that are running without any password or use a very weak password. After detecting a vulnerable router, it infects it and accesses the settings to replace the default DNS address with the address controlled by the attacker(s).
Researchers write that like DNSChanger, GhostDNS also tries to guess the password on the web authentication page of the router via the dnscfg.cgi exploit and then changes the default DNS address of the router with the Rogue DNS Server[3] via the “corresponding DNS configuration interface.”
“But this campaign has more, we have found three related DNSChanger programs, which we call Shell DNSChanger, Js DNSChanger, and PyPhp DNSChanger according to their programming languages,” explained researchers from NetLab.
The modular structure of the GhostDNS comprises four components, which are described below:
1: DNSChanger Module: It is the main module designed for exploiting the targeted routers and had three sub-modules titled: Shell DNSChanger, Js DNSChanger, and PyPhp DNSChanger.
Shell DNSChanger is a combination of 25 scripts written in Shell programming language and allows the malware to conduct brute-force attacks on firmware packages or routers from 21 different vendors.
Js DNSChanger: It is written in JavaScript and comprises 10 attack scripts. The scripts are designed to infect 6 routers/firmware packages including scanners, attack programs, and payload generators, while the program is injected into phishing websites.
To read the original article https://www.hackread.com/ghostdns-iot-malware-botnet-hits-banks/