According to a new report, three United States payment processing companies were targeted by BGP hijacking attacks on their DNS servers. These Internet routing attacks were designed to redirect traffic directed at the payment processors to servers controlled by malicious actors who would then attempt to steal the data.
On three separate dates in July, Oracle has stated that they saw what appeared to be BGP hijacks that targeted the DNS servers for U.S. payment processors Datawire, Vantiv, or Mercury Payment Systems.
According to Oracle, the first attack started on July 6th 2018 with a short duration attack that attempted to reroute the following network prefixes, or blocks of IP addresses. These attacks were targeting the Vantiv and Datawire payment processing companies.
64.243.142.0/24 Savvis
64.57.150.0/24 Vantiv, LLC - Vantiv
64.57.154.0/24 Vantiv, LLC - Vantiv
69.46.100.0/24 Q9 Networks Inc. - Datawire
216.220.36.0/24 Q9 Networks Inc. - DatawireOn July 10th another attack was conducted that tried to reroute the same prefixes, but according to Oracle, this time it lasted for 30 minutes. The attackers conducted further hijacks throughout July, including one attack on Mercury Payment Systems and another attack on Vantiv and Datawire that lasted as long as 3 hours.
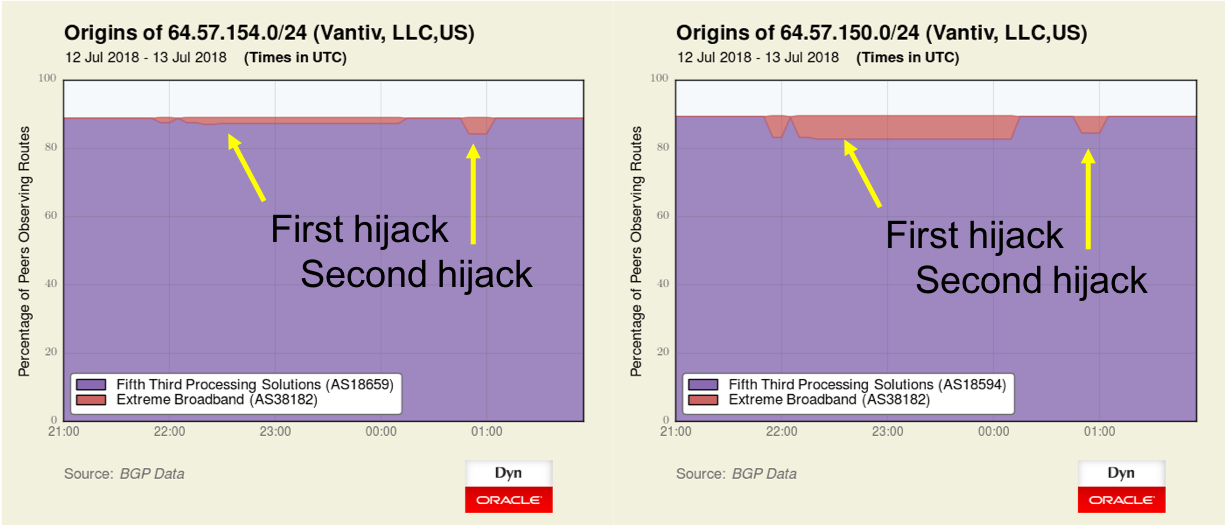
In two of the attacks on July 10th and 13th targeting Datawire, Oracle observed traffic being routed out of Luhansk in eastern Ukraine to IP addresses in Dutch Caribbean island of Curaçao.
Oracle thinks this may be just the beginning of these types of attacks.
« If previous hijacks were shots across the bow, these incidents show the Internet infrastructure is now taking direct hits, » Oracle’s research stated. « Unfortunately, there is no reason not to expect to see more of these types of attacks against the Internet. »
Similarities to Amazon AWS BGP hijack attack in April
In April 2018, Oracle noticed a similar attack against Amazon’s DNS servers that allowed caused traffic directed at one of their AWS customers, MyEtherWallet, to be redirected to a fake version of the site hosted in Russia. This attack allowed hackers to steal $160,000 USD worth of Ethereum.
This fake site was located in Germany, but like the attacks last month, was also routed out of Luhansk in eastern Ukraine.
This and other similarities, such as setting long TTLs, makes Oracle suspect that the two attacks may be related.
Bleeping Computer has reached out to WorldPay, Vantiv, and Datawire for comment, but had not heard back at the time of this publication.
To read the original article: