An organized and highly dynamic malware distribution campaign has been leveraging thousands of hacked websites to redirect users to web pages peddling fake software updates in an attempt to infect them with malware.
According to Jerome Segura, the Malwarebytes researcher who analyzed multiple infection chains to piece together the grander scheme, this campaign started four months ago, in December 2017.
Segura named the campaign « FakeUpdates » because all malicious sites would redirect users to web pages hosting update packages for various types of software, usually Google Chrome, Mozilla Firefox, Internet Explorer, or Adobe Flash Player.
Crooks stealing traffic from hacked sites
The crooks behind this campaign rely on hacked websites to hijack legitimate traffic for the fake update pages.
Segura says he observed most of the traffic coming from hacked WordPress, Joomla, and Squarespace sites , but the Malwarebytes researcher also says he spotted crooks leveraging other CMS platforms, as well, usually the ones running outdated versions that were vulnerable to attacks.
The way crooks hijacked traffic from these sites was by injecting JavaScript code inside already-existing JS files present on the site, or by loading a new JS file with the site altogether.
The role of this malicious JS code was to take the user through a series of automated redirects until he landed on other hacked websites where crooks were hosting the page with the fake update package. [see GIF below]
Fake updates deliver banking trojans, RATs
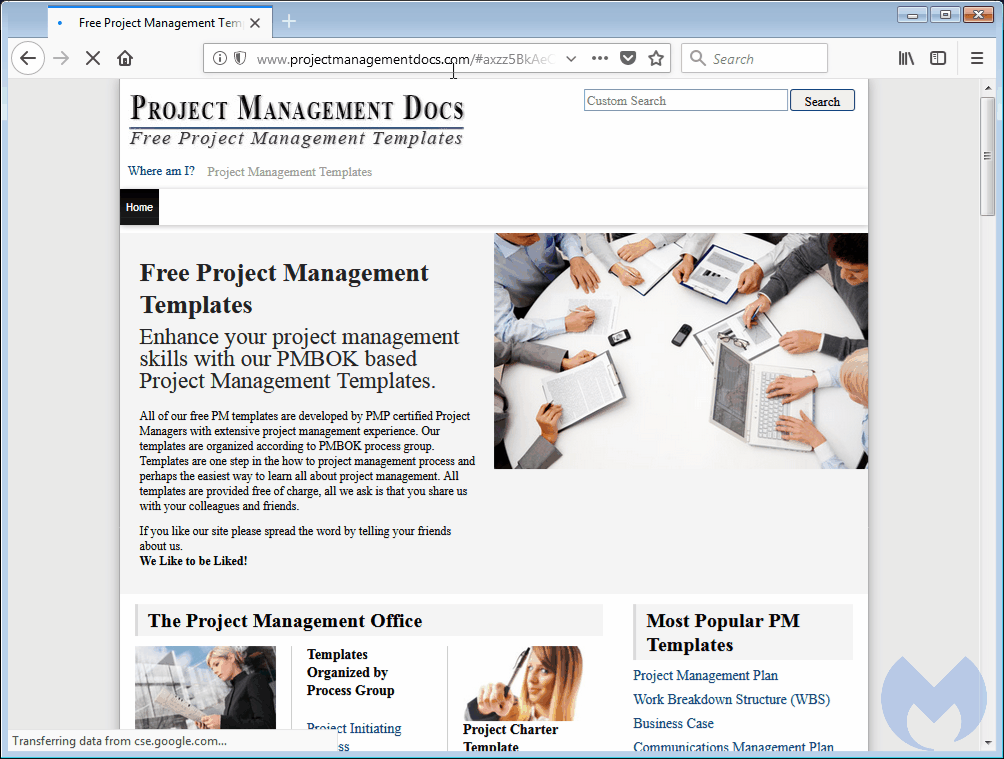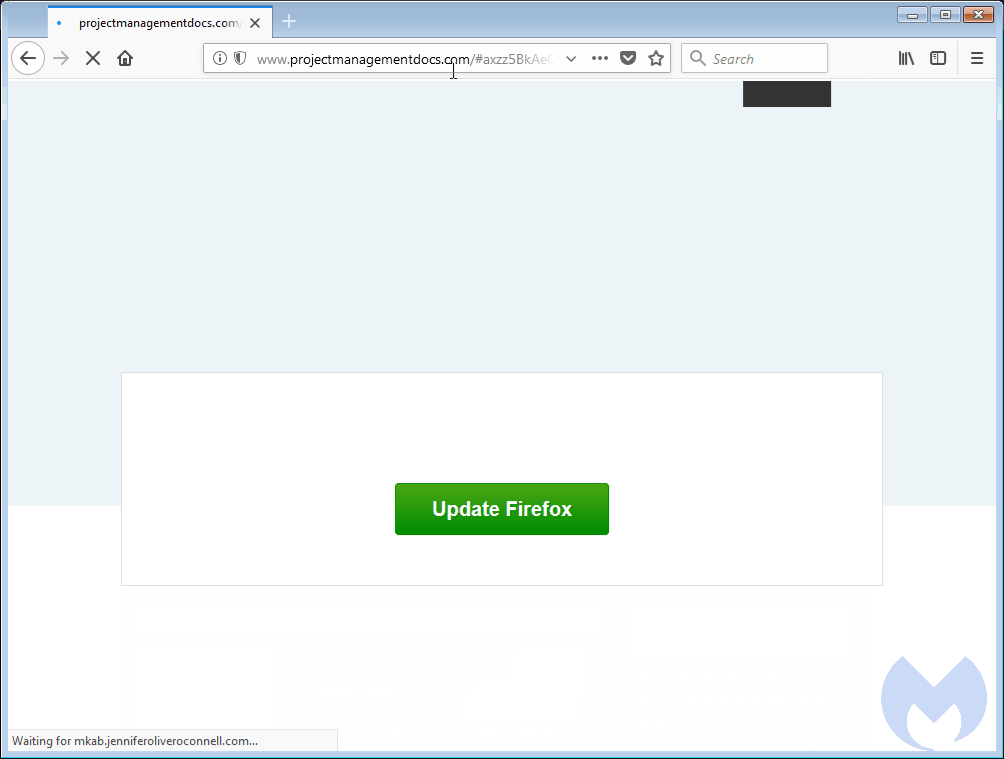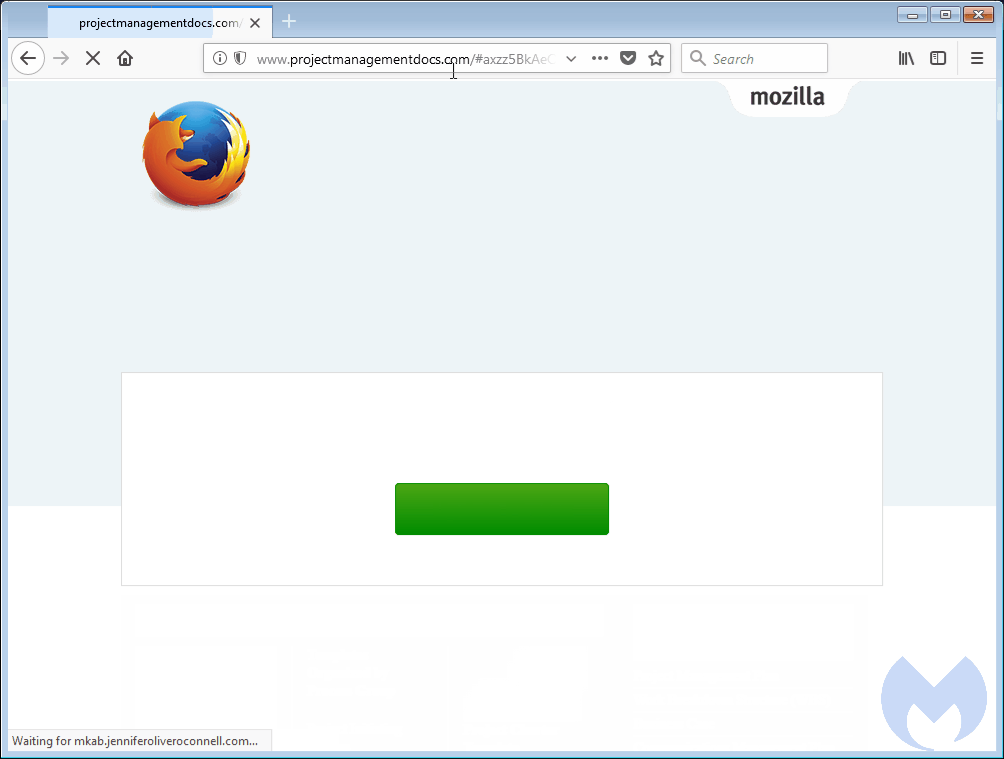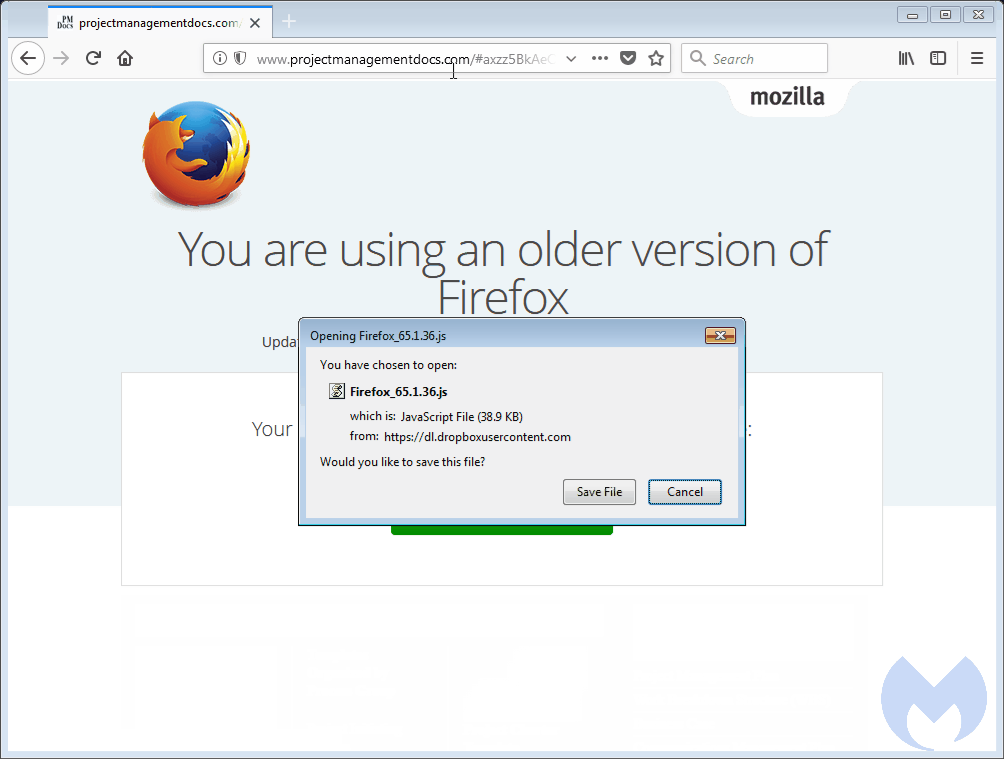
Users tricked into downloading the fake update packages didn’t receive an EXE file, but another JS script, usually hosted on a Dropbox link. Running the JS script would download and install the final malware payload.
Segura says that during his tests, the malware he received was the Chthonic banking trojan, but other reports also describe the FakeUpdates campaign dropping the NetSupport remote access trojan (RAT).
« The ‘bait’ file consists of a script rather than a malicious executable, giving the attackers the flexibility to develop interesting obfuscation and fingerprinting techniques, » Segura explains.
FakeUpdates is an evolution on past campaigns
Overall, the FakeUpdates malware delivery campaign is somewhat similar to what Bleeping Computer and other security researchers have been reporting in the past.
With the downfall of major exploit kits, crooks have turned to creating giant botnets of hacked sites and using traffic distribution systems to funnel legitimate traffic from these sites to malicious pages.
Over the past year, most of this hijacked traffic has gone to so-called « social engineering » web pages, a class of attacks that include classic tech support scams and browser (ransomware-like) lockers, but also sites leveraging the « fake update » trick.
The fake update gimmick is an old trick that came to rebecame popular once again last year, as exploit kits began to lose their popularity. But before the FakeUpdates campaign came to be, we first had websites trying to trick users into downloading missing font packs [1, 2, 3], a variation of the « fake update » trick.
As the year progressed, towards the end of 2017, the actual « fake update » shtick came into its own, with reports of campaigns leveraging Yahoo malvertising, hacked Magento sites, and GitHub repositories to fool users into downloading and installing malware-laced « fake updates. »
The FakeUpdates campaign is the result of more cybercrooks jumping on this most recent malware distribution trend, refining existing techniques, and building infrastructure to massive proportions as time passed by.
Nevertheless, as FakeUpdates got bigger, it also left more evidence behind that security researchers like Segura could put together and demystify its modus operandi. And with greater knowledge of how this campaign works, web and desktop-based security software can now be updated to counteract attempted attacks.
As « fake update » attacks will become less effective as more eyes from the infosec industry will focus on their operation, the trend will peak and die out for something new altogether in a constant game of cat and mouse between researchers like Segura and the mythical 400-pound hackers sitting at their computers in their moms’ basement.
To read the original article:
