A Chinese malware operation is currently building a massive botnet of nearly 5 million Android smartphones using a strain of malware named RottenSys.
In its current form, RottenSys is being used to aggressively display ads on users’ devices, but researchers from security firm Check Point have found evidence that crooks are deploying a new Lua-written module for gathering all infected handsets into a giant botnet.
« This botnet will have extensive capabilities including silently installing additional apps and UI automation, » researchers said, fearing that crooks may get brazen and abuse RottenSys for something more intrusive and damaging to the user, rather than just displaying ads on his screen.
RottenSys has been active since 2016
But RottenSys wasn’t always this dangerous. The malware first appeared in September 2016, and crooks spent most of their time spreading it to new devices.
Slowly but surely, the number of RottenSys victims grew as months past by, and according to Check Point, the malware is now on approximately 4,964,460 devices.
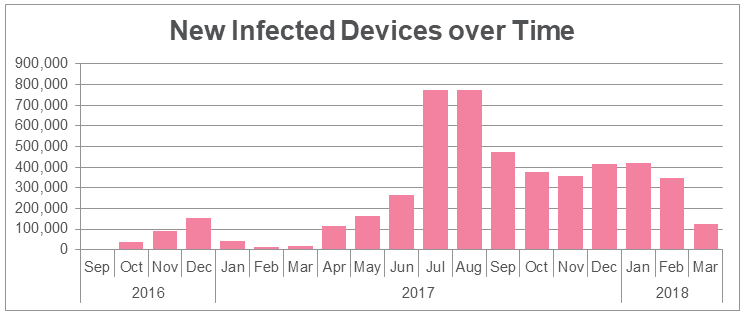
The dangerous botnet component that gives attackers control over all devices was added only last month, in February 2018, and for most of the past two years, the RottenSys crew has been focused on ad delivery.
Researchers estimate the malware authors are currently making around $115,000 every ten days, based on ad impressions they were able to observe during their analysis.
The malware is currently only active on the Chinese market, being bundled in Chinese apps, and infecting mostly phones popular on the local market, such as Huawei (over 1 million devices), Xiaomi (almost half a million devices), OPPO, vivo, LeEco, Coolpad, and GIONEE.
RottenSys uses virtualization and « undead » processes
There have been other Android malware families observed in the past, but few managed to infect so many devices. The reasons behind RottenSys’ success are found in its code.
The malware uses two open-source projects shared on GitHub —Small, an application virtualization framework; and MarsDaemon, a library that keeps apps « undead. »
First, RottenSys uses Small to create virtualized containers for its internal components, allowing them to run in parallel, at the same time —something that the Android OS does not natively support— and help with the app delivery process.
Second, RottenSys uses MarsDaemon to keep processes alive, even after users close them, making sure the ad injection mechanism cannot be turned off.
RottenSys active on the Chinese market
The only weak spot in the malware’s internal mode of operation is its installation routine. Apps infected with RottenSys tend to ask for a huge list of permissions. Attentive users can easily spot and avoid installing such apps. But, alas, not all Android users are privacy-conscious, and most day-to-day users will tend to give apps all the permissions they need.
Remind you; there’s no Google Play Store in China, so most users aren’t aware of proper Android security best practices and will install apps from shady third-party stores on a regular basis.
Despite RottenSys being a malware strain localized on the Chinese region, it’s use of the Small and MarsDaemon apps might become popular with other malware strains active across the world.
Furthermore, it is unclear how the RottenSys crew might use their newly-created botnet, and we may soon see it used for DDoS attacks, similar to how the WireX crew used their botnet before getting shut down by a coalition of security firms and law enforcement.
For what’s it worth, Check Point ended their technical report on the RottenSys malware by offering « to share additional technical details with law enforcement agencies and facilitate further mitigation of consumer risks. »
To read the original article:
