A new cryptocurrency-stealing malware dubbed as ComboJack has been discovered by Palo Alto Networks Unit 42 and Proofpoint researchers. It has been targeting cryptocurrencies and digital wallets belonging to American and Japanese users while the malware is being distributed via email spam campaign.
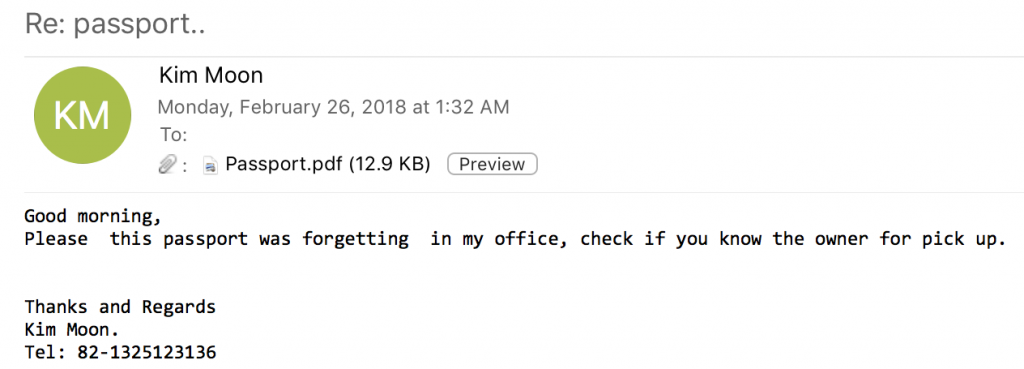
Fake Passport Email
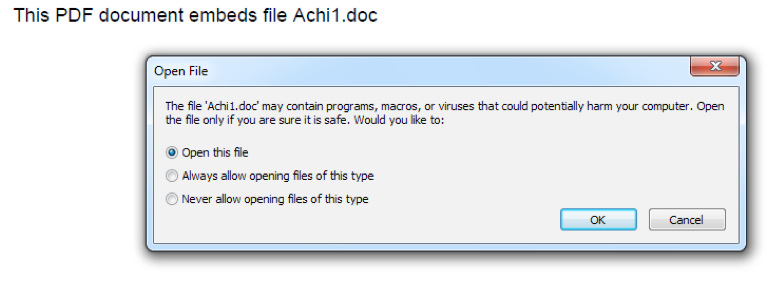
The malicious emails contain the subject line “Re: passport…” The attackers trick recipients into opening a PDF attachment that supposedly contains a scanned copy of a passport the recipient has mistakenly left in the email sender’s office. The file does not show the scanned passport image but displays a request to open another file, which is actually an embedded RTF file. This RTF file contains an embedded remote object.
This object attacks an old DirectX flaw (classified as CVE-2017-8579) and loads an HTA script. The script runs a PowerShell script to download the malware. Microsoft DirectX is basically a collection of APIs that manages multimedia related tasks on Windows OS.
After the malware is downloaded, it makes sure that it stays on the device for which it keeps itself hidden from the user. It then creates an infinite loop to keep checking the contents of the clipboard after half a second to assess what sorts of cryptocurrencies the victim has stored on his/her digital wallet.
Palo Alto Networks researchers noted in their blog post:
“The contents of the clipboard are checked for various criteria to determine if the victim has copied wallet information for various digital currencies. In the event a wallet of interest is discovered, ComboJack will replace it with a hardcoded wallet that the attacker presumably owns in an attempt to have the victim accidentally send money to the wrong location.”
ComboJack Replaces Clipboard Addresses
ComboJack replaces clipboard addresses to upload an attacker-operated address. Funds are then transferred to the attacker’s wallet instead of their actual address. The attack method relies upon the same tactic that was used by CryptoShuffler malware (identified in 2017). It also benefitted from victims’ ignorance in cross-checking the destination wallet address prior to making funds transfer.
To read the original article:
https://www.hackread.com/combojack-malware-steals-cryptocurrency-modifies-addresses/
