On February 22, 2018, Morphisec Labs spotted several malicious word documents exploiting the latest Flash vulnerability CVE-2018-4878 in the wild in a massive malspam campaign. Adobe released a patch early February, but cyber criminals know that is will take some companies weeks, months or even years to rollout the patch.
All the documents showed a very low detection ratio and successfully downloaded the next stage artifacts from a newly registered domain. Analyzing the attack, it became clear, that it took the attackers only a few and easy changes to the original targeted attack to outplay static defenses once more.
Note to Morphisec Customers: Morphisec prevents all variants of this attack, starting from the first version one and half years ago to this latest one leveraging CVE-2018-4878.
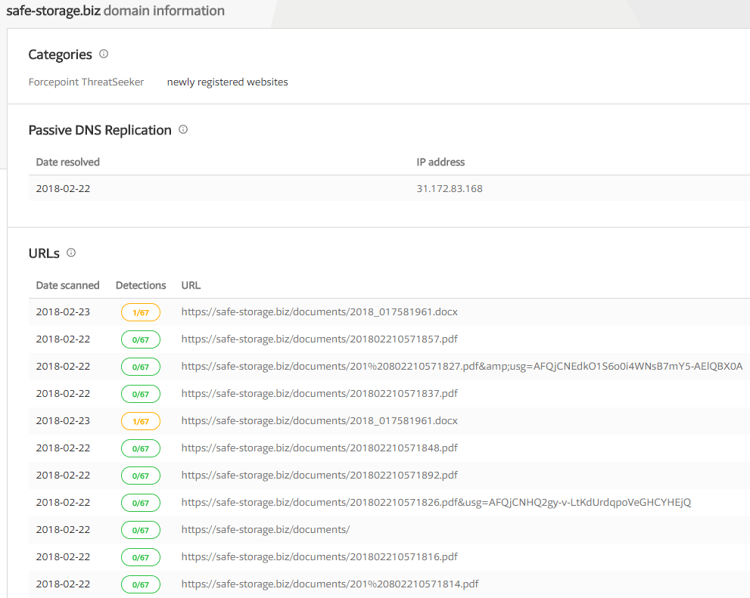
The documents were downloaded from the safe-storge[.]biz domain and went almost entirely undetected with an 1/67 detection ratio.
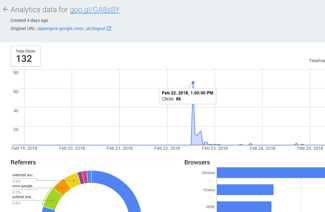
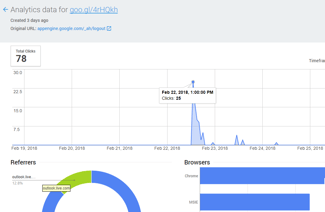
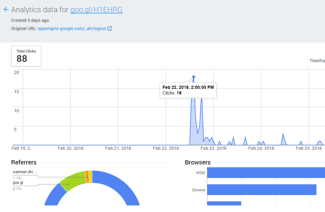
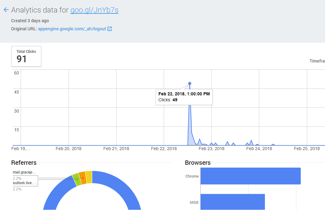
While many security defenses missed their goal, the attack did not. In the emails, the victims received short links to the malicious website generated by Google URL Shortener. This gives us the possibility to see the analytics for the short links, such as click rate and mail host used. We see e.g. that victims opened it through Outlook, Gmail and the Italian webhost Aruba.it. This is of course only a partial picture; we detected five different short links, but there are likely more.
The analytics for the short links shows the same pattern as legitimate email campaigns. Clickthroughs spike in the first couple of hours after emails are sent. Signature-based defenses, like anti-viruses, cannot cope with this pace.
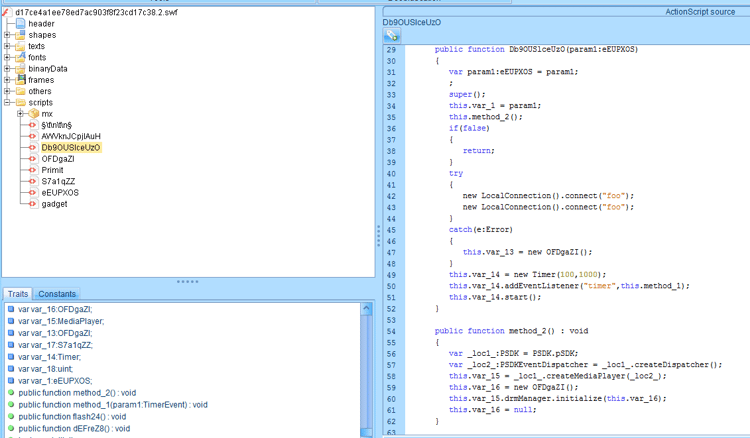
After downloading and opening the word document, the attack exploits the Flash vulnerability 2018-4878 and opens a cmd.exe which is later remotely injected with a malicious shellcode that connects back to the malicious domain.
Also the extracted SWF Flash file had very low detection score on VirusTotal:
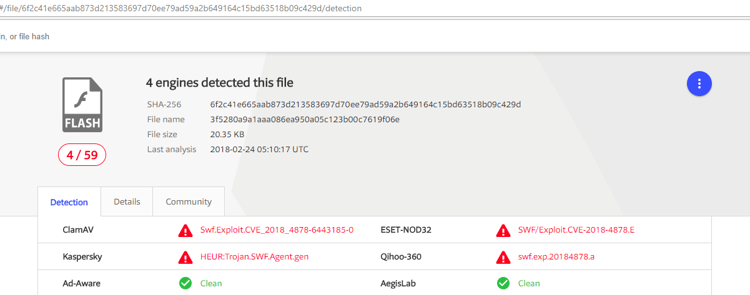
The disassembled Flash file had a very similar signature to existing PoCs with special similarity to the stripped 32 bit PoC. Different to the original attack, the current malspam campaign doesn’t have a 64 bit implementation.
Conclusion
As expected and predicted, the adversaries eagerly adopted the Flash exploit which is easily reproducible. With small variations to the attack they successfully launched a massive malspam campaign and bypassed most of the existing static scanning solutions once again.
Morphisec’s Endpoint Threat Prevention solution is agnostic to the morphing and obfuscation of the exploit, and prevented the exploit before any damage could occur.
To read the original article:http://blog.morphisec.com/flash-exploit-cve-2018-4878-spotted-in-the-wild-massive-malspam-campaign