A global mobile espionage campaign collecting a trove of sensitive personal information from victims since at least 2012 has accidentally revealed itself—thanks to an exposed server on the open internet.
It’s one of the first known examples of a successful large-scale hacking operation of mobile phones rather than computers.
The advanced persistent threat (APT) group, dubbed Dark Caracal, has claimed to have stolen hundreds of gigabytes of data, including personally identifiable information and intellectual property, from thousands of victims in more than 21 different countries, according to a new report from the Electronic Frontier Foundation (EFF) and security firm Lookout.After mistakenly leaking some of its files to the internet, the shadowy hacking group is traced back to a building owned by the Lebanese General Directorate of General Security (GDGS), one of the country’s intelligence agencies, in Beirut.
« Based on the available evidence, it’s likely that the GDGS is associated with or directly supporting the actors behind Dark Caracal, » the report reads.
According to the 51-page-long report , the APT group targeted « entities that a nation-state might attack, » including governments, military personnel, utilities, financial institutions, manufacturing companies, defence contractors, medical practitioners, education professionals, academics, and civilians from numerous other fields.
Researchers also identified at least four different personas associated with Dark Caracal’s infrastructure — i.e. Nancy Razzouk, Hassan Ward, Hadi Mazeh, and Rami Jabbour — with the help of email address op13@mail[.]com.
« The contact details for Nancy present in WHOIS information matched the public listing for a Beirut-based individual by that name. When we looked at the phone number associated with Nancy in the WHOIS information, we discovered the same number listed in exfiltrated content and being used by an individual with the name Hassan Ward. »
Multi-Platform Cyber Espionage Campaign
However, since at least 2012, the group has run more than ten hacking campaigns aimed mainly at Android users in at least 21 countries, including North America, Europe, the Middle East and Asia.
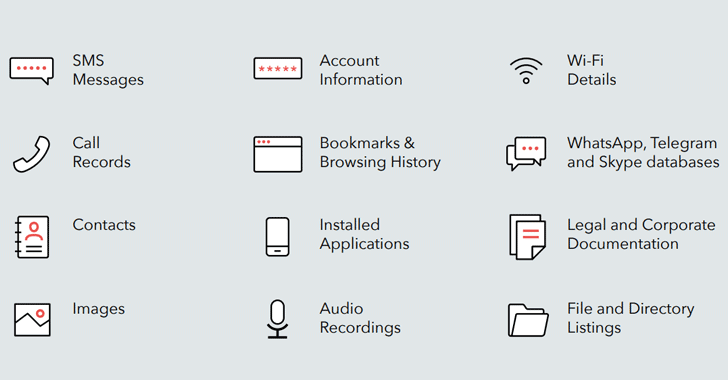
The data stolen by Dark Caracal on its targets include documents, call records, text messages, audio recordings, secure messaging client content, browsing history, contact information, photos, and location data—basically every information that allows the APT group to identify the person and have an intimate look at his/her life.