A team of security researchers has discovered a critical implementation flaw in major mobile banking applications that left banking credentials of millions of users vulnerable to hackers.
The vulnerability was discovered by researchers of the Security and Privacy Group at the University of Birmingham, who tested hundreds of different banking apps—both iOS and Android—and found that several of them were affected by a common issue, leaving their users vulnerable to man-in-the-middle attacks.
The affected banking apps include HSBC, NatWest, Co-op, Santander, and Allied Irish bank, which have now been updated after researchers reported them of the issue.
According to a research paper published by researchers, vulnerable applications could have allowed an attacker, connected to the same network as the victim, to intercept SSL connection and retrieve the user’s banking credentials, like usernames and passwords/pincodes—even if the apps are using SSL pinning feature.
SSL pinning is a security feature that prevents man-in-the-middle (MITM) attacks by enabling an additional layer of trust between the listed hosts and devices.
When implemented, SSL pinning helps to neutralize network-based attacks wherein attackers could attempt to use valid certificates issued by rogue certification authorities.
« If a single CA acted maliciously or were compromised, which has happened before, valid certificates for any domain could be generated allowing an attacker to Man-in-the-Middle all apps trusting that CA certificate, » the researchers wrote in their paper.
However, there are two key parts to verify an SSL connection—the first (authentication) is to verify whether the certificate is from a trusted source and the second (authorization) is to make sure the server you are connecting to presents the right certificate.
Researchers found that due to lack of hostname verification, several banking applications were not checking if they connected to a trusted source.
Verifying a hostname ensures the hostname in the URL to which the banking app connects matches the hostname in the digital certificate that the server sends back as part of the SSL connection.
« TLS misconfiguration vulnerabilities are clearly common; however none of the existing frameworks will detect that a client pins a root or intermediate certificate, but fails to check the hostname in the leaf, » the paper reads.
Besides this issue, the researchers also detailed an « in-app phishing attack » affecting Santander and Allied Irish Banks, which could have allowed attackers to hijack part of the victim’s screen while the app was running and use it to phish for the victim’s login credentials.
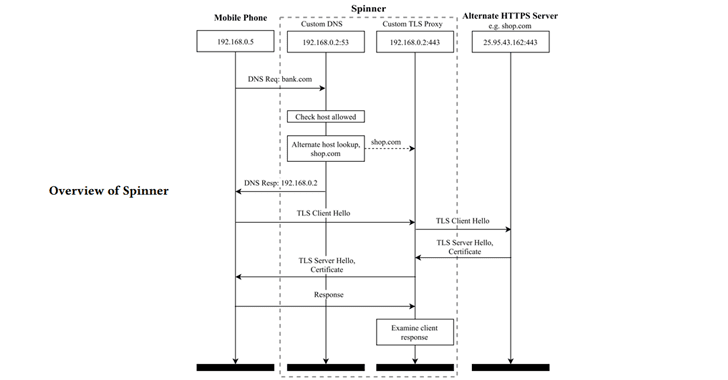
Spinner leverages Censys IoT search engine for finding certificate chains for alternate hosts that only differ in the leaf certificate.
To read the original article:
https://thehackernews.com/2017/12/mitm-ssl-pinning-hostname.html
